Last Updated On : 13-Jan-2026
Total 64 Questions
Device discovery information is stored in which database?
A. CMDB
B. Profile DB
C. Event DB
D. SVN DB
Explanation:
The Configuration Management Database (CMDB) in FortiSIEM is the central repository for all configuration and asset-related information within the monitored environment. When FortiSIEM's discovery engine scans the network, all the detailed information it collects about devices—such as IP addresses, hostnames, device type, operating system, hardware details, and installed software—is automatically populated into the CMDB. This database is then used by the correlation engine for context, by analysts for incident investigation, and for reporting and configuration management.
Correct Option:
A. CMDB (Configuration Management Database):
The CMDB is the designated database for storing static and configuration-related data about the discovered assets in the infrastructure.
The discovery process, which includes gathering device type, vendor, IP, hostname, and configuration details, is specifically designed to populate the CMDB.
This information provides the essential context needed for event normalization, correlation rule processing, incident investigation, and risk scoring.
Incorrect Options:
B. Profile DB:
The Profile DB (Profile Database), typically an SQLite database on the Supervisor node, is used to store calculated system data and risk data.
This includes baselines for performance monitoring, anomaly detection datasets (e.g., UEBA profiles), and various internal metrics, but it is not the storage location for the raw device inventory and configuration information gathered during discovery.
C. Event DB:
The Event DB (Event Database), which can be FortiSIEM's proprietary NoSQL DB or a ClickHouse/Elasticsearch cluster, is dedicated to storing the massive volume of raw and normalized event logs and performance monitoring metrics.
Its purpose is historical data retention and searching, not maintaining the static or semi-static inventory details collected through device discovery.
D. SVN DB:
The SVN DB (Subversion Database, often referred to as a version control system) in FortiSIEM is primarily used to store the historical and current configuration files (CLI-based config backups) collected from network devices.
While it stores configuration data, it's a versioned repository for files (e.g., show running-config), whereas the CMDB stores the structured and categorized discovery information (asset records) itself.
Reference:
FortiSIEM 6.3 Administration Guide: CMDB and FortiSIEM Database Options sections.
Consider the storage of anomaly baseline date that is calculated for different parameters. Which database is used for storing this data?
A. Event DB
B. Profile DB
C. SVNDB
D. CMDB
Explanation:
FortiSIEM calculates anomaly baselines for parameters like traffic volumes, device CPU/memory usage, and login patterns using historical data aggregated over time windows (e.g., 7-30 days). These baselines, including means, standard deviations, and thresholds, are stored in the CMDB to enable real-time comparisons against incoming events for anomaly detection. This integration with the CMDB ensures baselines are tied to specific devices, users, and configurations discovered in the inventory, supporting UEBA and performance analytics without overloading event storage.
Correct Option:
D – CMDB
The CMDB (Configuration Management Database) serves as the central repository for all discovered assets, performance metrics, and derived analytics like anomaly baselines.
Baselines are computed periodically by the Supervisor and Workers, then persisted in CMDB tables (e.g., perf_metrics_baseline) for quick lookups during rule evaluation.
This design allows scalable anomaly detection across distributed environments, as baselines are device-specific and updated dynamically based on CMDB inventory changes.
Incorrect Option:
A – Event DB
The Event DB (typically NoSQL on NFS or Elasticsearch/ClickHouse) is optimized for raw event ingestion, storage, and querying, handling high-volume logs and metrics.
It does not store computed baselines; instead, it provides the raw data source for baseline calculations, but retaining all historical data there would inefficiently consume storage.
B – Profile DB
The Profile DB (phoenix_config or similar) primarily holds user-defined configurations like rules, reports, dashboards, and notification policies.
While it supports some analytics profiles, anomaly baselines are not stored here; confusing it with CMDB is common, but baselines are asset-linked data in CMDB for operational use.
C – SVNDB
SVNDB is a version control repository (Subversion-based) used for tracking changes to custom parsers, scripts, and configuration files over time.
It has no role in storing runtime analytics data like baselines; it's solely for development and auditing code/config evolutions, not performance or anomaly metrics.
Reference:
FortiSIEM 6.3.0 Administration Guide → System Architecture → "Database Overview" and "Anomaly Detection" sections (pages 45-52, 678-685).
How is a subpattern for a rule defined?
A. Filters, Aggregation, Group by definitions
B. Filters, Group By definitions, Threshold
C. Filters, Threshold, Time Window definitions
D. Filters, Aggregation, Time Window definitions
Explanation:
In FortiSIEM analytics, a rule's subpattern is a core building block that defines a specific set of matching events. It acts as a filter to identify relevant events from the incoming stream based on criteria like source, destination, or event type, and then groups and counts them according to the rule's logic. Multiple subpatterns can be combined within a single correlation rule to define complex sequences or conditions.
Correct Option:
Option A:
This is correct. A subpattern is fundamentally defined by:
Filters: To select specific events based on attributes (e.g., eventType = "Firewall Accept").
Aggregation: To define how to count the filtered events (e.g., Count, Sum, Average, Distinct Count of a field).
Group By: To segment the aggregated counts by specific attributes (e.g., by srcIP to see counts per source IP address).
Incorrect Options:
Option B:
This is incorrect because it omits Aggregation, which is essential. A subpattern must define an aggregation function (like Count) to quantify the filtered events. "Threshold" is a parameter of the overall rule that acts upon the results of the subpattern(s), not a defining component of the subpattern itself.
Option C:
This is incorrect. While "Time Window" is a critical rule parameter that specifies over what period to evaluate the subpattern, it is a rule-level setting, not part of the subpattern's internal definition. "Threshold" is also a rule-level condition, not a subpattern component.
Option D:
This is incorrect because, similar to Option C, it incorrectly includes Time Window definitions as part of the subpattern. The subpattern defines what and how to aggregate, while the rule's time window defines when.
Reference:
Fortinet FortiSIEM Analytics Guide, specifically the sections on creating correlation rules and defining subpatterns. The official documentation outlines that a subpattern configuration consists of Event Filters, a Group By clause, and an Aggregation function.
An administrator wants to search for events received from Linux and Windows agents. Which attribute should the administrator use in search filters, to view events received from agents only.
A. External Event Receive Protocol
B. Event Received Proto Agents
C. External Event Receive Raw Logs
D. External Event Receive Agents
Explanation:
Purpose: The External Event Receive Agents field is a specific FortiSIEM metadata attribute that records how an event was received. It specifically indicates that the event was ingested via the FortiSIEM Agent protocol.
Agent vs. Syslog/SNMP Trap: FortiSIEM receives events through multiple channels:
Agents: The FortiSIEM Agent (FS Agent) installed on Windows or Linux hosts.
Syslog: Direct syslog messages from network devices, firewalls, etc.
SNMP Trap: Trap messages from SNMP-managed devices.
Why D is Correct: To search for events that came specifically from Windows or Linux agents, you must filter on the reception method. Using External Event Receive Agents in your search filter will return only those events sent via the agent protocol, automatically including events from both Windows and Linux agents.
Why the Others are Incorrect:
A. External Event Receive Protocol:
This field shows the protocol (e.g., TCP, UDP, RELP) used to receive the event, but not whether it came from an agent. A syslog message could also be received via TCP.
B. Event Received Proto Agents:
This is not a standard FortiSIEM event attribute name.
C. External Event Receive Raw Logs:
This field typically contains the original, unparsed log message as it was received. It is used for viewing the raw data, not for filtering by source type.
Reference:
This relates directly to understanding FortiSIEM's event metadata and data ingestion paths, a core topic covered in the FortiSIEM Administration and Analyst curriculum regarding event collection and filtering.
Refer to the exhibit.
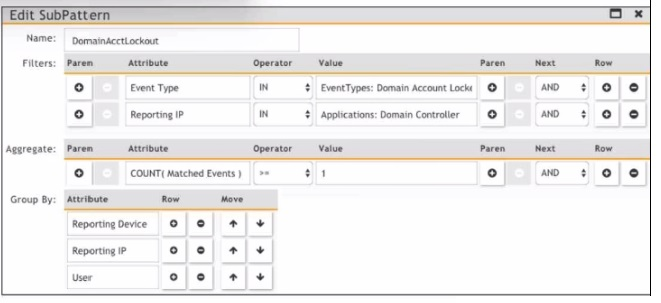
Which section contains the sortings that determine how many incidents are created?
A. Actions
B. Group By
C. Aggregate
D. Filters
Explanation:
In FortiSIEM correlation rules, the "Group By" section directly determines how incidents are grouped and counted. Here's why:
Purpose of "Group By": This section defines the event attributes used to segment or bucket the matched events. Each unique combination of values in the "Group By" fields will trigger a separate incident.
How it Works: The rule engine applies the Filters to find matching events. It then takes those matching events and groups them based on the attributes specified in "Group By". If you have Reporting Device and User in Group By, then events for Device_A, User_X will create one incident, and events for Device_A, User_Y will create a different incident, even if they occur at the same time.
Relationship to Incident Count:If you set no Group By fields, all matching events will be aggregated into a single incident. Adding Group By fields (like Reporting Device, User, etc.) increases the potential number of incidents by creating separate incidents per unique grouping.
Why the Others Are Incorrect:
A. Actions:
This section defines what to do when an incident is created (send email, run script, etc.), not how incidents are grouped.
C. Aggregate:
This section defines the time window and count threshold (e.g., "5 events within 60 seconds"). It determines when an incident is triggered based on event volume, but it does not determine how many separate incidents are created—that is the function of Group By.
D. Filters:
This section determines which events are selected for the rule to process. It defines the event criteria but does not control the grouping into distinct incidents.
Reference:
FortiSIEM Administrator Guide - "Creating Correlation Rules," specifically the sections explaining the function of the Group By clause in incident creation.
FortiSIEM is deployed in disaster recovery mode. When disaster strikes, which two tasks must you perform manually to achieve a successful disaster recovery operation? (Choose two.)
A. Promote the secondary workers to the primary roles using the phSecworker2priworker command.
B. Promote the secondary supervisor to the primary role using the phSecondary2primary command.
C. Change the DNS configuration to ensure that users, devices, and collectors log in to the secondary FortiSIEM.
D. Change the configuration for shared storage NFS configured for EventDB to the secondary FortiSIEM.
Explanation:
When FortiSIEM is deployed in Disaster Recovery (DR) mode, the system includes a primary supervisor and a secondary supervisor (standby). Upon disaster, manual intervention is required to promote the secondary and redirect traffic.
Here are the two critical manual steps:
B. Promote the secondary supervisor to the primary role using phSecondary2primary
This CLI command is mandatory to switch the secondary supervisor into active mode. It updates internal roles and ensures the secondary takes over event processing and system coordination.
C. Change the DNS configuration to ensure that users, devices, and collectors log in to the secondary FortiSIEM
DNS redirection is essential so that all external systems (collectors, agents, users) now point to the new active supervisor. Without this, traffic still targets the failed primary.
❌ Why Others Are Wrong:
A. phSecworker2priworker:
This command is not required in DR mode. Workers automatically reconnect to the promoted supervisor. Manual promotion of workers is only relevant in non-DR or custom deployments.
D. NFS reconfiguration:
In DR mode, shared storage (EventDB) is already accessible to both supervisors. No manual change is needed unless the storage itself is compromised — which is outside the scope of standard DR failover.
📖 Reference:
FortiSIEM Admin Guide 6.3, section:
Disaster Recovery Deployment and Failovereference
Fortinet KB:
FortiSIEM Disaster Recovery CLI Commands
In the advanced analytical rules engine in FortiSIEM, multiple subpatterms can be referenced using which three operation?(Choose three.)
A. ELSE
B. NOT
C. FOLLOWED_BY
D. OR
E. AND
Explanation:
FortiSIEM's advanced analytical rules engine uses a pattern-based correlation language where subpatterns are combined using specific temporal and logical operators to define complex attack scenarios or conditions.
B. NOT:
This is a logical operator used to specify the absence of a subpattern within a defined time window. It is essential for creating rules that detect when a specific event does not happen as expected (e.g., authentication failure NOT followed by a success).
C. FOLLOWED_BY:
This is a temporal/sequential operator. It defines a strict order where one subpattern must occur after another subpattern within a specified timeframe. This is critical for modeling multi-stage attack sequences (e.g., a vulnerability scan FOLLOWED_BY an exploitation attempt).
E. AND:
This is a logical operator used to specify that multiple subpatterns must occur within the same time window, but without a required order. It detects the co-occurrence or conjunction of events (e.g., a suspicious file download AND an outbound connection attempt).
Why the others are incorrect:
A. ELSE:
This is not a valid operator in FortiSIEM's advanced rule syntax. The rule logic is built using explicit pattern-matching operators, not procedural conditional statements like IF-THEN-ELSE.
D. OR: While OR is a fundamental logical operator, it is not typically used as a direct operator to combine subpatterns in the advanced analytical rule definition interface. Instead, to achieve an "OR" condition, you typically create separate subpatterns or use multiple filter conditions within a single subpattern. The primary operators for chaining distinct subpatterns together are AND, FOLLOWED_BY, and NOT.
Reference:
FortiSIEM Administrator Guide, section on "Creating Advanced Analytical Rules" or "Using the Analytical Rules Engine." The official documentation lists and explains these specific operators.
| Page 2 out of 10 Pages |
| NSE5_FSM-6.3 Practice Test Home |
Choosing the right preparation material is critical for passing the Fortinet NSE 5 - FortiSIEM 6.3 exam. Here’s how our NSE5_FSM-6.3 practice test is designed to bridge the gap between knowledge and a passing score.