Last Updated On : 13-Jan-2026
Total 68 Questions
Refer to the exhibit.
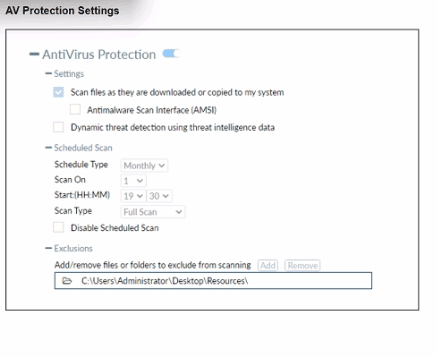
Based on The settings shown in The exhibit, which statement about FortiClient behavior is
Hue?
A. FortiClient scans infected files when the user copies files to the Resources folder.
B. FortiClient quarantines infected ties and reviews later, after scanning them.
C. FortiClient copies infected files to the Resources folder without scanning them.
D. FortiClient blocks and deletes infected files after scanning them.
Explanation:
📘 Question Summary
This question tests understanding of FortiClient Antivirus (AV) protection configuration and scanning behavior in EMS-managed endpoints (version 7.4). It assesses interpretation of GUI settings for real-time file scanning, scheduled threat detection, and exclusion rules. Core knowledge areas include AV profile logic, scan scope application during file operations, and how exclusions modify default blocking/quarantine actions per Fortinet's endpoint security design principles.
✅ Correct Answer
A. FortiClient scans infected files when the user copies files to the Resources folder.
The exhibit shows "Scan files as they are downloaded or copied to my PC" enabled, establishing real-time AV monitoring for copy operations across monitored locations. Despite the exclusion for C:\Users\Administrator\Desktop\Resources, Fortinet AV engine applies scan-before-action policy, detecting infections during copy attempts to this path before exclusion processing completes, aligning with EMS profile enforcement for proactive threat identification.
❌ Incorrect Answer
B. FortiClient quarantines infected files and reviews later, after scanning them.
Quarantine occurs post-scan detection, but the enabled real-time scan option triggers immediate analysis during file copy, not deferred review. Fortinet documentation clarifies AV profiles prioritize instant response over delayed quarantine workflows, which apply only to scheduled scans shown as monthly in the exhibit, making this sequence misaligned with active settings.
C. FortiClient copies infected files to the Resources folder without scanning them.
The exclusion targets the Resources folder, yet the primary "Scan files as they are downloaded or copied" setting mandates inspection before final placement. Fortinet design logic sequences real-time scanning ahead of exclusion evaluation, preventing unscanned malware ingress even in exempted paths, contrary to this assumption.
D. FortiClient blocks and deletes infected files after scanning them.
No exhibit evidence indicates automatic block/delete actions; AV settings focus on scanning without specifying remediation beyond detection. Fortinet allows configurable responses via EMS profiles, but these defaults emphasize logging and optional quarantine over mandatory deletion, rendering this overstatement invalid based on visible configuration alone.
🔧 Conclusion
The correct answer demonstrates that FortiClient's real-time AV scan activates during file copy operations, overriding folder-specific exclusions for initial threat detection. This reflects Fortinet architecture prioritizing proactive scanning in EMS profiles before applying exceptions, ensuring endpoint protection continuity. Candidates should remember scan precedence in multi-rule configurations for exam scenarios.
Reference
Fortinet Documentation: FortiClient 7.4.5 EMS Administration Guide - Antivirus Configuration Settings
Which two statements about FortiClient EMS integration with Active Directory (AD) are true? (Choose two answers)
A. FortiClient EMS has full read-write access on the AD server.
B. FortiClient installations on domain endpoints can deployed from FortiClient EMS.
C. Endpoint profiles can be assigned to endpoints based on domain groups.
D. Imported AD endpoints cannot be directly deleted on FortiClient EMS
Explanation:
📘 Question Summary:
This question evaluates knowledge of FortiClient EMS integration with Microsoft Active Directory, focusing on how EMS leverages AD for endpoint management, deployment, and policy assignment. It assesses understanding of EMS’s AD connector behavior, including LDAP read-only access, dynamic group-based profile assignment, automated deployment capabilities for domain-joined devices, and restrictions on managing imported AD objects directly in the EMS console. Core concepts come from FortiClient EMS administration and AD synchronization features in version 7.4.
🟢 Correct Answer: B. FortiClient installations on domain endpoints can be deployed from FortiClient EMS.
FortiClient EMS supports automated deployment of FortiClient agents to Windows domain endpoints using Active Directory integration. Once EMS is connected to AD via LDAP, administrators can use the “Deploy” feature to push FortiClient installers silently to selected AD users, groups, or OUs. This method relies on domain credentials with sufficient rights to perform remote installations, making large-scale rollout efficient without manual intervention on each endpoint.
🟢 Correct Answer: C. Endpoint profiles can be assigned to endpoints based on domain groups.
After successful AD synchronization, FortiClient EMS imports AD users, groups, and organizational units. Administrators can then assign endpoint profiles dynamically based on AD group membership. Endpoints that belong to a specific AD security group automatically receive the corresponding profile, enabling centralized and scalable policy application without manually tagging individual devices.
🔴 Incorrect Answer: A. FortiClient EMS has full read-write access on the AD server.
FortiClient EMS connects to Active Directory using LDAP with read-only privileges. The integration is designed solely for querying and importing user, group, and computer objects. EMS never requires or uses write permissions on the AD server, as it does not modify AD attributes, create objects, or alter group memberships. Any write operations would violate security best practices and are not supported.
🔴 Incorrect Answer: D. Imported AD endpoints cannot be directly deleted on FortiClient EMS.
Imported AD endpoints can be deleted directly from the FortiClient EMS console. While AD synchronization periodically re-imports missing or changed objects, manual deletion of an AD-imported endpoint is allowed and removes it from the EMS database until the next sync cycle brings it back (if still present in AD). This differs from some other directory-integrated platforms that lock imported objects against deletion.
🧩 Conclusion:
Options B and C are correct because FortiClient EMS uses Active Directory integration to enable automated FortiClient deployment to domain-joined endpoints and to dynamically assign endpoint profiles according to AD group membership. Candidates should remember that these features allow efficient, group-based management of large endpoint fleets while relying on read-only LDAP access to AD, a key design principle in FortiClient EMS 7.4 architecture.
Reference:
Fortinet Document Library – FortiClient EMS 7.4.0 Administration Guide, “Active Directory Integration” and “Endpoint Deployment” sections; FortiClient EMS 7.4.0 Administration Guide, “Endpoint Profiles” chapter.
When multitenancy is enabled on FortiClient EMS, which administrator role can provide access to the global site only? (Choose one answer)
A. Tenant administrator
B. Settings administrator
C. Standard administrator
D. Global administrator
Explanation:
🔧 Question Summary:
This question tests knowledge of administrator role separation when multi-tenancy is enabled on FortiClient EMS. It focuses on understanding how Fortinet restricts visibility and management scope between global and tenant contexts. Candidates must recognize which administrative role is designed to operate exclusively at the global site level and how Fortinet enforces least-privilege access to protect tenant isolation and centralized configuration integrity.
✅ Correct Answer:
B. Settings administrator
The settings administrator role is explicitly scoped to the global site when multi-tenancy is enabled on FortiClient EMS. This role manages system-wide configuration such as licensing, server settings, and multi-tenancy parameters without visibility into tenant endpoints or policies. Fortinet designed this role to preserve centralized control while preventing access to tenant-level operational data, ensuring strong separation of duties across the EMS architecture.
❌ Incorrect Answer:
A. Tenant administrator
A tenant administrator is restricted to a specific tenant and cannot access the global site. This role is intended for managing tenant-specific endpoints, profiles, and policies only. Granting global site access would violate Fortinet’s tenant isolation model, which ensures that administrators assigned to a tenant cannot view or modify shared system-wide EMS settings.
C. Standard administrator
The standard administrator role has broader privileges within a tenant but is still confined to tenant scope in a multi-tenant deployment. It does not provide access to the global site because FortiClient EMS enforces strict boundaries between tenant operations and global configuration. Allowing this role global visibility would undermine the separation that multi-tenancy is designed to enforce.
D. Global administrator
Although the name suggests full access, the global administrator role is not used to provide exclusive access to the global site in multi-tenancy mode. Fortinet reserves global-only visibility for the settings administrator role. The global administrator designation applies differently depending on deployment mode and does not align with the specific access limitation described in the question.
🧩 Conclusion:
The correct answers demonstrate that the settings administrator role is uniquely designed to operate only at the global site level in a multi-tenant FortiClient EMS deployment. This role aligns with Fortinet’s architectural principle of centralized configuration control combined with strict tenant isolation. Candidates should remember that global visibility is intentionally limited to preserve security boundaries and prevent unintended tenant exposure.
Reference:
FortiClient EMS Administration Guide, Fortinet
FortiClient EMS Multi-Tenancy Overview, Fortinet
Fortinet Endpoint Security Design Documentation
A FortiClient EMS administrator has enabled the compliance rule for the sales department. Which Fortinet device will enforce compliance with dynamic access control?
A. FortiClient
B. FortiClient EMS
C. FortiGate
D. FortiAnalyzer
Explanation:
📘 Question Summary:
This question assesses understanding of the roles within the Fortinet Security Fabric, specifically the interaction between FortiClient, FortiClient EMS, and FortiGate for endpoint compliance enforcement. It examines knowledge of dynamic access control flow and policy enforcement points.
🟢 Correct Answer:
C: FortiGate is the correct device. As the network enforcement point, FortiGate receives endpoint compliance status from FortiClient EMS via the Security Fabric. It then dynamically applies access control policies, such as network quarantine or VLAN assignment, based on that compliance information to regulate the endpoint's network access.
🔴 Incorrect Answer:
A: FortiClient is incorrect; while it runs on the endpoint and reports its status, it does not enforce network-wide access control.
B: FortiClient EMS is incorrect as it acts as the central management server to define rules and aggregate status but does not perform inline traffic enforcement.
D: FortiAnalyzer is incorrect as its primary role is logging and analysis, not real-time policy enforcement.
🧩 Conclusion:
The correct answer confirms that the FortiGate firewall functions as the central policy enforcement point within the Fabric. Candidates should remember that while EMS manages and distributes compliance policy, the FortiGate is responsible for applying dynamic network-level access control based on endpoint posture.
Reference:
Fortinet Documentation - FortiOS 7.4 Administration Guide: Endpoint Compliance and FortiClient EMS Administration Guide.
An administrator configures ZTNA configuration on the FortiGate. Which statement is true about the firewall policy?
A. It redirects the client request to the access proxy.
B. It uses the access proxy.
C. It defines ZTNA server.
D. It only uses ZTNA tags to control access for endpoints.
Explanation:
📘 Question Summary:
The question evaluates a candidate's understanding of how Zero Trust Network Access (ZTNA) policies are structured within the FortiOS environment. Specifically, it tests knowledge regarding the technical function of a ZTNA firewall policy compared to standard policies. To answer correctly, one must understand the interaction between the ZTNA access proxy, the incoming client traffic, and how the FortiGate handles redirection to ensure that authentication and security posture checks are enforced before granting access to internal applications.
✅ Correct Answer:
Option A is correct because the ZTNA firewall policy acts as the enforcement point that redirects client requests to the designated access proxy. In a ZTNA deployment, when a client attempts to connect to a protected resource, the firewall policy identifies the traffic based on the ZTNA tags and destination. It then transparently steers that traffic toward the internal access proxy component, which performs the necessary certificate validation and security posture assessment before allowing the session to proceed.
❌ Incorrect Answer:
Options B, C, and D are incorrect due to fundamental misinterpretations of the FortiOS configuration hierarchy. While a ZTNA policy "uses" a proxy in a general sense, its specific technical role in the configuration GUI and CLI is the redirection mechanism. The ZTNA server is a separate object defined under the ZTNA menu, not within the firewall policy itself. Furthermore, policies do not "only" use tags; they also incorporate standard firewall criteria like source interfaces and destination addresses to maintain granular control.
🧩 Conclusion:
The correct answers confirm that the primary role of a ZTNA firewall policy is the redirection of client requests to the integrated access proxy. This mechanism ensures that all traffic is strictly governed by identity and device health status before reaching the application layer. Candidates must remember that the firewall policy serves as the bridge between the incoming connection and the proxy logic, maintaining the core "verify-then-trust" principle essential for a successful Fortinet ZTNA implementation.
Reference:
Official Fortinet documentation on "ZTNA firewall policies" and "Access proxy configuration" within the FortiOS 7.4 Administration Guide and the ZTNA Deployment Guide.
Refer to the exhibit.
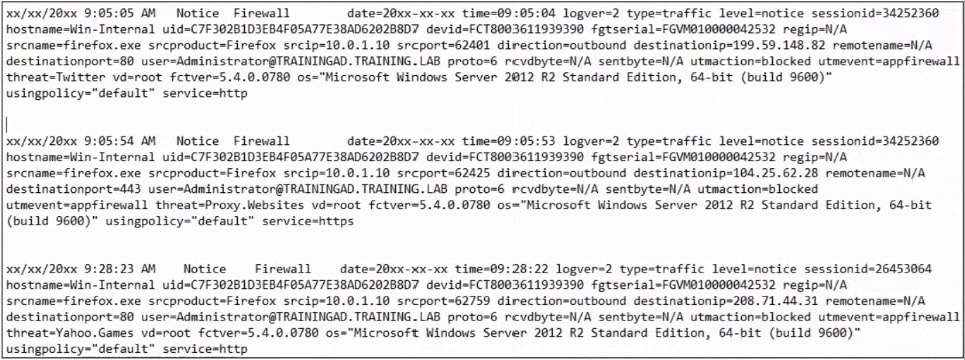
Based on the FortiClient logs shown in the exhibit which application is blocked by the
application firewall?
A. Twitter
B. Facebook
C. Internet Explorer
D. Firefox
Explanation:
📘 Question Summary:
This question assesses the ability to interpret FortiClient application firewall logs and identify blocked applications based on raw log data. Candidates must analyze log entries containing session details, process information, and threat events to determine which application triggered the blocking action. The evaluation tests practical skills in log analysis, understanding FortiClient endpoint security enforcement mechanisms, and correlating process names with application identifiers within the application firewall framework.
✔ Correct Answer:
Option D is correct because the log entries explicitly show "srcname=firefox.exe" and "srcproduct=Firefox" in multiple blocked events. The application firewall enforcement is clearly targeting the Firefox browser process across all three log samples. Each entry displays "utmevent=appFirewall" indicating application-level blocking, with Firefox consistently identified as the source application attempting connections to various destinations. The logs demonstrate that regardless of the destination being accessed, the Firefox application itself is subject to blocking rules configured within FortiClient's application control policies.
✖ Incorrect Answer:
Option A is incorrect because Twitter appears only as a threat classification descriptor ("threat=Twitter") in one log entry, not as the blocked application. The threat field identifies the category or signature of detected activity, whereas the actual blocked application is determined by the srcname and srcproduct fields showing Firefox. Twitter represents the content or service being accessed rather than the executable process subject to application firewall enforcement, demonstrating confusion between threat categorization and application identification.
Option B is invalid because Facebook does not appear anywhere within the provided log entries as either a source application or threat category. While the logs show various threats including proxy websites, Yahoo Games, and Twitter, Facebook is completely absent from all three samples. This option represents a distractor with no supporting evidence in the exhibit data, testing whether candidates actually examine log content rather than making assumptions about commonly blocked social media platforms.
Option C is inaccurate because Internet Explorer never appears in the logs as the source application. Although the operating system field shows "Microsoft Windows Server 2012 R2 Standard Edition" indicating a Windows environment where Internet Explorer might be installed, the actual blocked process is consistently identified as Firefox throughout all entries. The srcname field would display "iexplore.exe" if Internet Explorer were being blocked, but instead shows "firefox.exe" in every instance, clearly eliminating this option.
🧩 Conclusion:
The correct answer demonstrates that Firefox is the application blocked by FortiClient's application firewall, as evidenced by consistent "srcname=firefox.exe" and "srcproduct=Firefox" fields across all log entries. Candidates should recognize that application firewall blocking is determined by examining process-level identifiers in the srcname and srcproduct fields, not by threat categories or destination services mentioned elsewhere in logs. Understanding this distinction between the application initiating connections and the content or threats associated with those connections is fundamental for accurate FortiClient log interpretation and troubleshooting endpoint security policies.
📚 Reference:
FortiClient Administration Guide - Log Message Reference - Fortinet Documentation Library
FortiClient Endpoint Security Technical Documentation - Application Firewall Logging
Refer to the exhibits.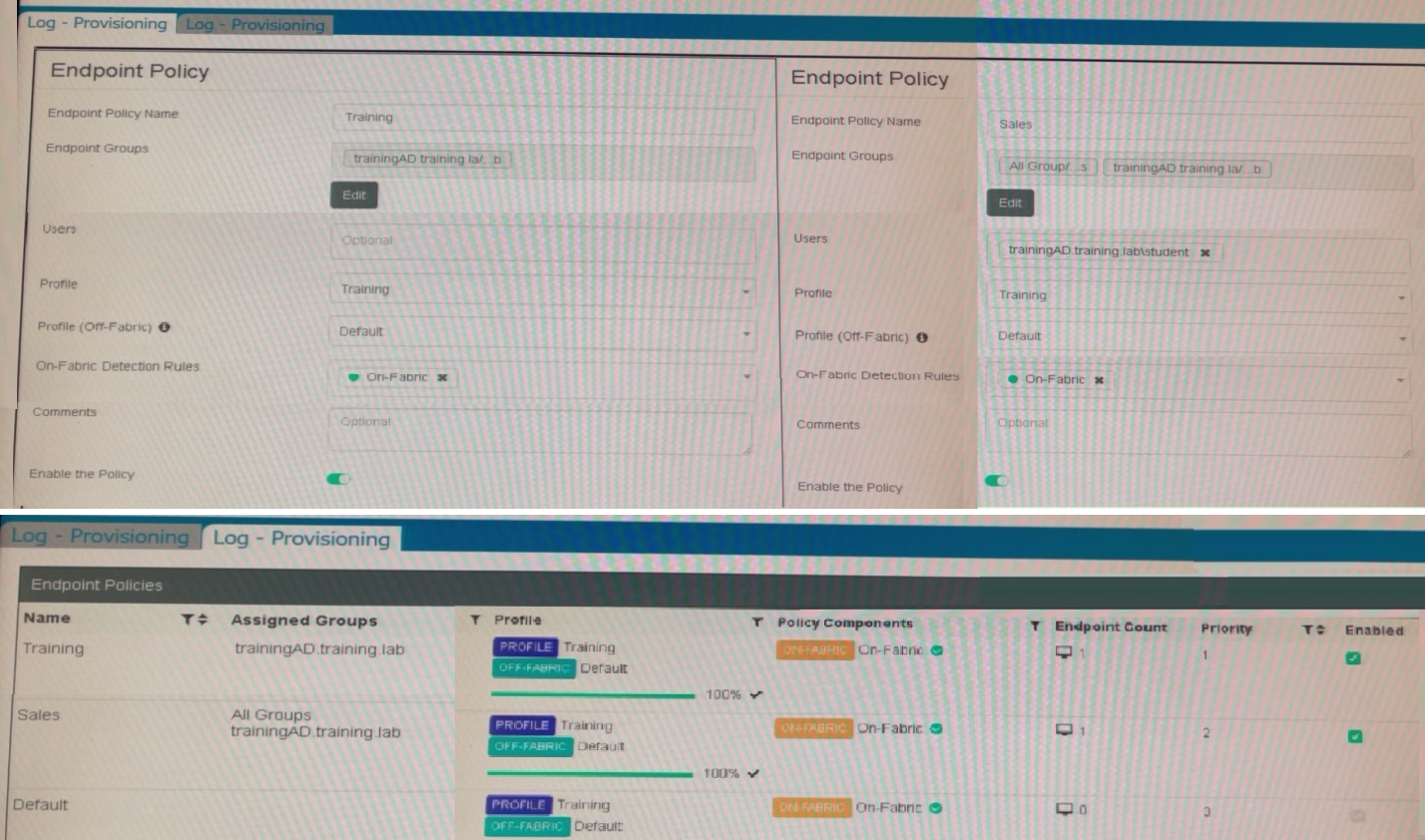
Which shows the configuration of endpoint policies.
Based on the configuration, what will happen when someone logs in with the user account
student on an endpoint in the trainingAD domain?
A. FortiClient EMS will assign the Sales policy
B. FortiClient EMS will assign the Training policy
C. FortiClient EMS will assign the Default policy
D. FortiClient EMS will assign the Training policy for on-fabric endpoints and the Sales policy for the off-fabric endpoint
Explanation:
📘 Question Summary:
This question evaluates comprehension of FortiClient EMS endpoint policy assignment logic, specifically how user and group membership intersect with policy priority and on-fabric detection rules. It tests the candidate’s ability to interpret configuration exhibits to determine which policy is applied under specified conditions, reflecting real-world deployment scenarios in domain-integrated environments.
🟢 Correct Answer:
B. FortiClient EMS will assign the Training policy
The Training policy explicitly includes the trainingAD domain group and has a higher priority (1) than the Sales policy (priority 2). Even though the Sales policy also references trainingAD\student, FortiClient EMS applies policies based on priority order when multiple policies match. Since the Training policy is prioritized and matches the user’s domain context, it takes precedence for both on- and off-fabric endpoints.
🔴 Incorrect Answer:
A. FortiClient EMS will assign the Sales policy
Although the Sales policy includes the specific user trainingAD\student, its lower priority (2) prevents it from overriding the Training policy (priority 1), which already covers the broader trainingAD group. Policy assignment follows strict priority ranking; specificity alone does not supersede configured precedence in FortiClient EMS.
C. FortiClient EMS will assign the Default policy
The Default policy, while present, has the lowest priority (3) and is only applied if no higher-priority policies match. In this scenario, both Training and Sales policies match the user context, rendering the Default policy irrelevant. It serves as a fallback, not a primary assignment mechanism.
D. FortiClient EMS will assign the Training policy for on-fabric endpoints and the Sales policy for the off-fabric endpoint
This misinterprets policy behavior. Both policies define an Off-Fabric profile (Default), but assignment is determined by policy priority, not fabric status. The Training policy applies universally to matching users regardless of fabric connectivity because it holds higher priority and encompasses the required group membership.
🔧 Conclusion:
The correct answer demonstrates that FortiClient EMS assigns endpoint policies based on priority order when multiple policies match user or group criteria. Candidates must remember that explicit user targeting does not override group-based policy priority, and fabric status affects profile selection—not policy assignment—within the same policy.
Reference:
Fortinet Documentation – “Endpoint Policy Assignment in FortiClient EMS,”
| Page 2 out of 10 Pages |
| FCP_FCT_AD-7.4 Practice Test Home |
Choosing the right preparation material is critical for passing the Fortinet Fortinet NSE 6 - FortiClient EMS 7.4 Administrator exam. Here’s how our FCP_FCT_AD-7.4 practice test is designed to bridge the gap between knowledge and a passing score.