Last Updated On : 3-Mar-2026
Total 41 Questions
The smartest way to prepare for your Fortinet FCP_FMG_AD-7.6 exam isn't just reading—it's practicing. Our Fortinet FortiManager 7.6 Administrator practice test bridge gap, transforming your knowledge into a passing score. Familiarize yourself with the exact style and difficulty of the real Fortinet FCP_FMG_AD-7.6 practice questions, so there are no surprises. Get detailed feedback to identify your strengths and target your weaknesses, making your study time more efficient.
What is the purpose of ADOM revisions?
A. ADOM revisions find unused, duplicate, and unnecessary firewall policies and objects.
B. ADOM revisions show specific changes in a policy package when it is installed.
C. ADOM revisions compare previous snapshots of the Policy Package and ADOM-level objects with the device-level database.
D. ADOM revisions save the current state of all policy packages and objects for an ADOM.
Explanatin:
In FortiManager, an ADOM revision is essentially a snapshot of the configuration state at a given point in time.
When you create a revision, FortiManager saves the entire ADOM’s policy packages, objects, and settings.
This allows administrators to roll back, audit, or compare configurations later.
Official Fortinet documentation confirms: “ADOM revisions are snapshots of the ADOM database, including all policy packages and objects.” (FortiManager 7.6 Admin Guide).
❌ Why the other options are wrong
A. Find unused, duplicate, and unnecessary firewall policies and objects
That’s the role of Policy Consistency Check and Object Usage tools, not ADOM revisions.
B. Show specific changes in a policy package when it is installed
That’s handled by the Install Preview / Install Wizard, which shows diffs before pushing to devices.
C. Compare previous snapshots of the Policy Package and ADOM-level objects with the device-level database
That’s the function of Policy Package Diff / Device Database comparison, not ADOM revisions.
📖 Reference
Fortinet FortiManager 7.6 Administration Guide – “ADOM revisions are snapshots of the ADOM database, including all policy packages and objects. They can be used to restore or compare configurations.”
Refer to the exhibit.
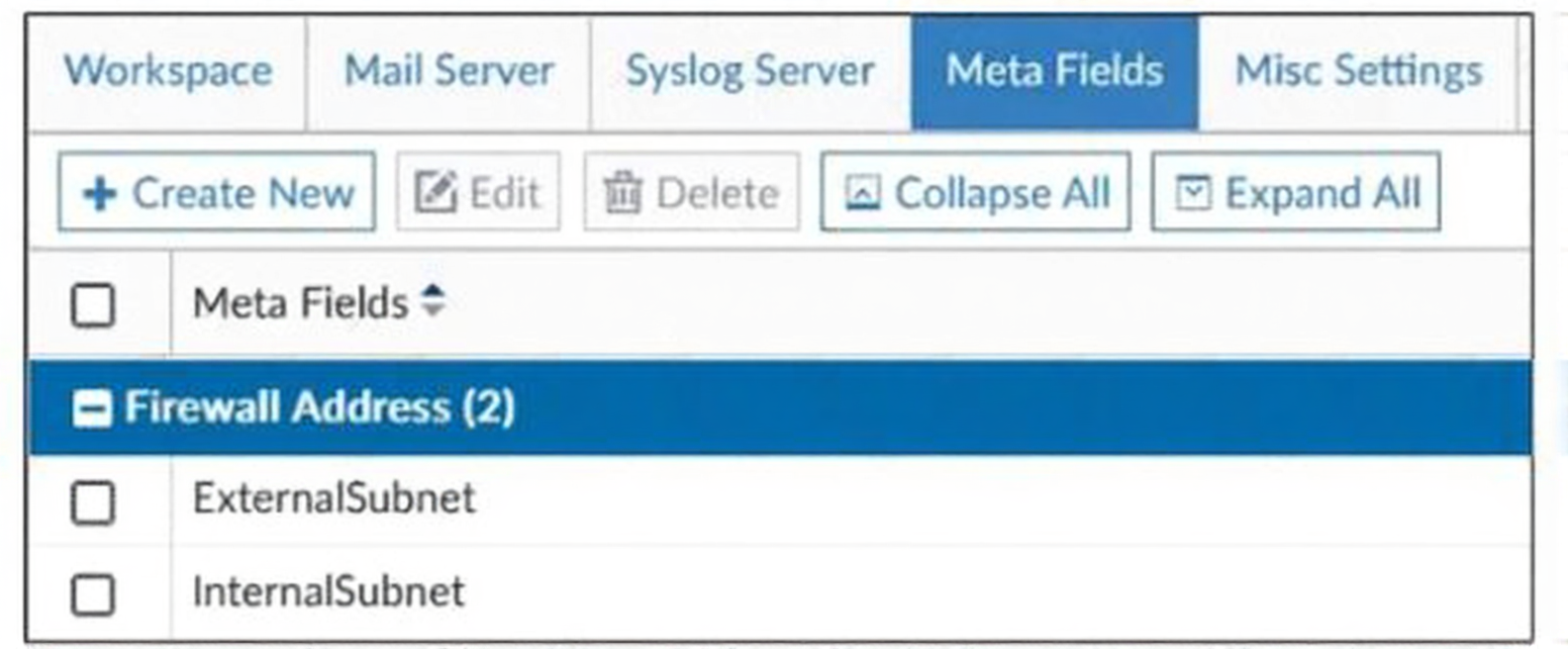
An administrator created two new meta fields in FortiManager.
Which operation can you perform with these parameters?
A. You can add them to objects as custom attributes.
B. You can export them to be used in other ADOMs.
C. You can use them as variables in scripts.
D. You can invoke them using the $ character.
Explanation:
The exhibit clearly shows two meta fields—ExternalSubnet and InternalSubnet—created under the “Firewall Address” category in an ADOM’s Meta Fields configuration. Meta fields are custom tags or attributes that administrators can define and then assign to specific objects or policies to enhance organization, filtering, and reporting. In this case, these fields can be attached to address objects (like IPv4 addresses, ranges, or subnets) to classify them by their network role, making policy management more intuitive and searchable.
Option B is incorrect
because meta fields are scoped to the ADOM in which they are created. They are not global objects and cannot be exported or shared directly between ADOMs. Each ADOM maintains its own independent set of meta fields.
Option C is incorrect
because meta fields are descriptive labels, not script variables. Variables used in FortiManager CLI scripts are defined separately as “Script Variables” or “Custom Attributes” within the Device Manager or policy package, not in the Meta Fields section.
Option D is incorrect
as it refers to the syntax used for referencing Custom Attributes (${attribute_name}) or CLI script variables in device configuration templates. Meta fields are not invoked using the $ character; they are used within the GUI for metadata tagging and filtering.
Reference:
FortiManager 7.6 Administration Guide > Policy & Objects > Meta Fields. The guide states, “Meta fields are custom fields that you can add to policy objects and policies. You can use meta fields to sort, group, and filter policies and objects in the policy list.” This aligns with the function shown in the exhibit: creating custom fields to annotate firewall address objects.
Refer to the exhibit.
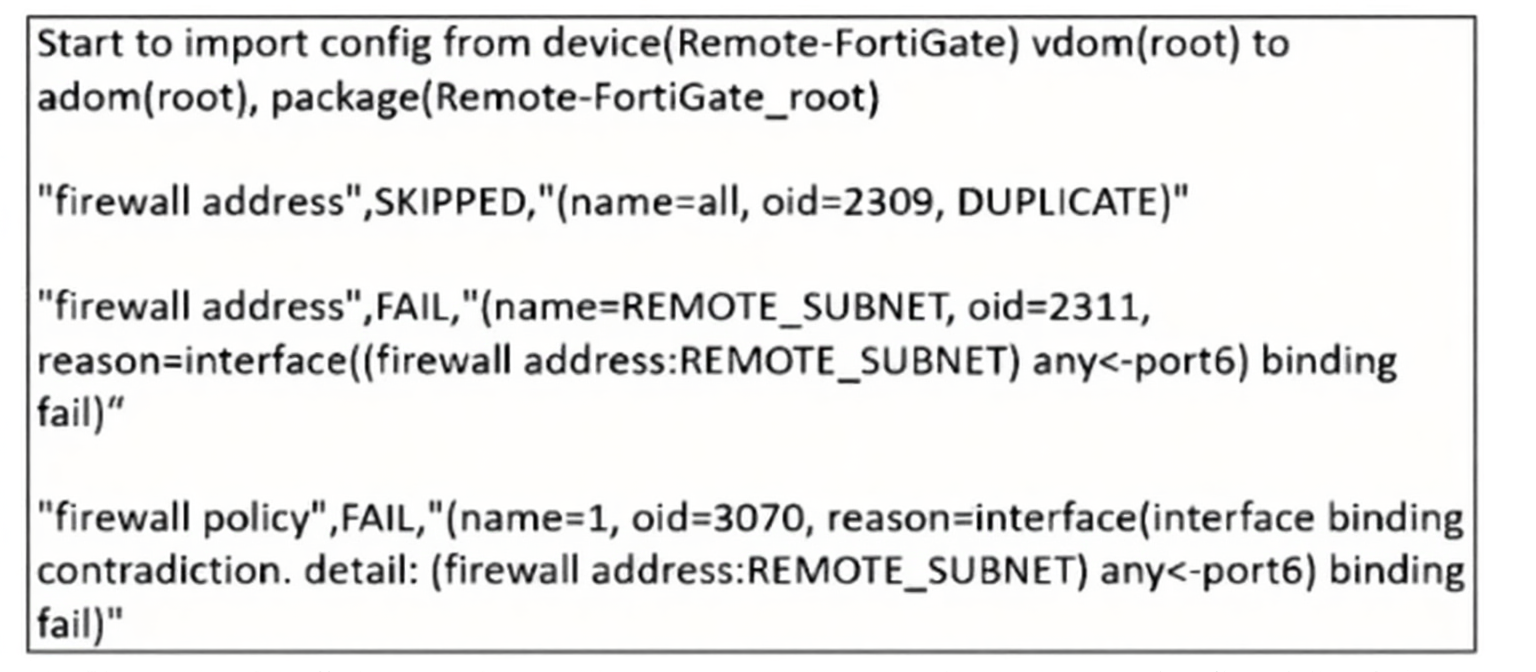
What can you conclude from the downloaded import report?
A. FortiManager does not support per-device mapping for firewall addresses.
B. The administrator will see a new policy package named Remote-FortiGate_root in the FortiManager ADOM database.
C. FortiManager will change the configuration of REMOTE_SUBNET to match the interface mapping coming in from Remote-FortiGate.
D. As a result of this policy import process, FortiManager will create a new firewall address called REMOTE_SUBNET in the ADOM database.
Explanation:
The import process shown is a Policy & Object import, which creates a new policy package in the specified ADOM (root) using the device’s configuration. The header explicitly states the target package as Remote-FortiGate_root, confirming a new package will be created. The subsequent SKIP and FAIL entries detail object-level import results within that package.
Option A is incorrect
because per-device mapping is fully supported and is precisely what caused the REMOTE_SUBNET failure; the system attempted to map the device’s interface (port6) but encountered a binding conflict.
Option C is incorrect
as the REMOTE_SUBNET object import FAILED; FortiManager does not force a change when interface mapping fails. The conflict must be resolved manually.
Option D is incorrect
because the report clearly states the firewall address REMOTE_SUBNET failed to import due to an interface binding error, so it will not be created in the ADOM database.
Reference:
FortiManager 7.6 Administration Guide > Device & Console > Installing Policies and Objects > Importing Policies and Objects from Devices. The import function creates a new policy package, and the import report indicates success or failure for each configuration object, with interface mapping being a common point of failure.
You want to let multiple administrators work in the same ADOM without creating configuration conflicts.
What is the best and the most effective solution to apply?
A. Configure RADIUS authentication to assign ADOM roles to each user.
B. Enable workflow mode, which is the only way to prevent concurrent configuration conflicts.
C. Assign administrators with JSON API access to the FortiManager.
D. Activate workspace mode in the ADOM settings.
Explanation:
Workspace mode is the native FortiManager feature specifically designed to allow multiple administrators to work concurrently in the same ADOM without overwriting each other's changes. When enabled, each admin works in an isolated, private workspace where they can make and validate configuration changes. Changes are only committed to the public ADOM database when the admin explicitly submits their workspace for approval, preventing direct configuration conflicts.
Option A is incorrect.
While RADIUS authentication and role-based access control are important for defining permissions, they do not inherently prevent two authorized admins from editing the same policy or object at the same time, which can lead to conflicts and overwrites.
Option B is incorrect.
Workflow mode is used for change approval processes (requiring a second admin to review and install changes), not for preventing concurrent editing conflicts. Workspace mode is the primary mechanism for conflict prevention during the configuration phase.
Option C is incorrect.
The JSON API is an automation interface; providing API access does nothing to prevent manual configuration conflicts and could even increase the risk if not managed properly.
Reference:
FortiManager Administration Guide — Workspace Mode. The guide states workspace mode allows administrators to "make changes to the ADOM database without interfering with other administrators' work" and that changes are "isolated until they are submitted," making it the best solution for concurrent work.
A service provider administrator has assigned a global policy package to a managed customer ADOM named My_ADOM. The customer administrator has access only to My_ADOM. How can the customer administrator edit the global header policy of the global policy package?
A. The customer administrator can edit the header policy by using workspace mode on the global ADOM.
B. The customer administrator can edit the header policy by using workflow mode on the global ADOM and My_ADOM.
C. The service provider administrator can unlock the global policy from the global ADOM to authorize changes to the customer administrator.
D. The customer administrator cannot edit the global header policy; only the service provider administrator can make changes from the global ADOM.
Explanation:
Global policy packages are created and managed in the Global ADOM.
The header and footer policies in a global policy package are enforced across all assigned ADOMs.
These policies are read-only from the perspective of the customer ADOM. The customer administrator can see them but cannot modify them.
Only the service provider administrator (who has access to the Global ADOM) can edit or update the global header/footer policies.
Fortinet documentation states: “Global policy packages are managed in the Global ADOM. Administrators of assigned ADOMs cannot modify global header or footer policies.” (FortiManager 7.6 Admin Guide).
❌ Why the other options are wrong
A. Workspace mode on the global ADOM
Workspace mode allows collaborative editing and commit control, but the customer administrator does not have access to the Global ADOM.
B. Workflow mode on the global ADOM and My_ADOM
Workflow mode is for approval processes, but again, the customer administrator cannot access the Global ADOM.
C. Service provider administrator can unlock the global policy
There is no “unlock” mechanism to delegate editing of global header policies to customer administrators. Control remains strictly with the service provider.
📖 Reference
FortiManager 7.6 Administration Guide – “Global policy packages are defined in the Global ADOM. Only administrators with access to the Global ADOM can edit global header and footer policies. ADOM-level administrators cannot modify them.”
An administrator has a FortiGate-HQ device with VDOMs—root, HR and Facilities, currently managed under the FortiManager ADOM—Site1. They try to move VDOM HR to the FortiManager ADOM—Site2, but it does not work. Why is the administrator not able to move FortiGate-HQ VDOM HR to FortiManager ADOM—Site2?
A. The FortiGate-HQ must be managed under the FortiManager ADOM—root to allow moving its VDOMs to different ADOMs.
B. The administrator must have full access in the device layer of FortiGate-HQ VDOM-root before they can VDOMs to different ADOMs.
C. FortiManager must be in ADOM normal mode, which does not allow VDOMs to be managed separately.
D. The administrator must delete the FortiGate-HQ device from FortiManager and add it again using the Add Device wizard before moving the VDOM.
Explanation:
FortiManager supports per-VDOM management, but only if the FortiGate device itself is registered under the root ADOM.
When a FortiGate with multiple VDOMs is added to a non-root ADOM (like Site1 in this case), all of its VDOMs are bound to that ADOM. You cannot split them across multiple ADOMs.
To manage VDOMs separately across different ADOMs, the FortiGate must be added under the root ADOM, then each VDOM can be assigned to different ADOMs.
Fortinet documentation states: “To manage VDOMs in separate ADOMs, the FortiGate must be added to the root ADOM. If added to another ADOM, all VDOMs remain bound to that ADOM.” (FortiManager 7.6 Admin Guide).
❌ Why the other options are wrong
B. Full access in device layer of VDOM-root
Access rights have no bearing on ADOM assignment. The limitation is architectural, not permissions-based.
C. FortiManager must be in ADOM normal mode
Normal mode does allow per-VDOM management, but only if the device is added under root ADOM. The issue is not the mode but the ADOM assignment.
D. Delete and re-add using Add Device wizard
Re-adding the device alone won’t solve the problem unless it’s added under the root ADOM. The wizard doesn’t bypass the ADOM binding rule.
📖 Reference
FortiManager 7.6 Administration Guide – “When a FortiGate is added to a non-root ADOM, all VDOMs are bound to that ADOM. To manage VDOMs in separate ADOMs, the FortiGate must be added to the root ADOM.”
Refer to the exhibit.
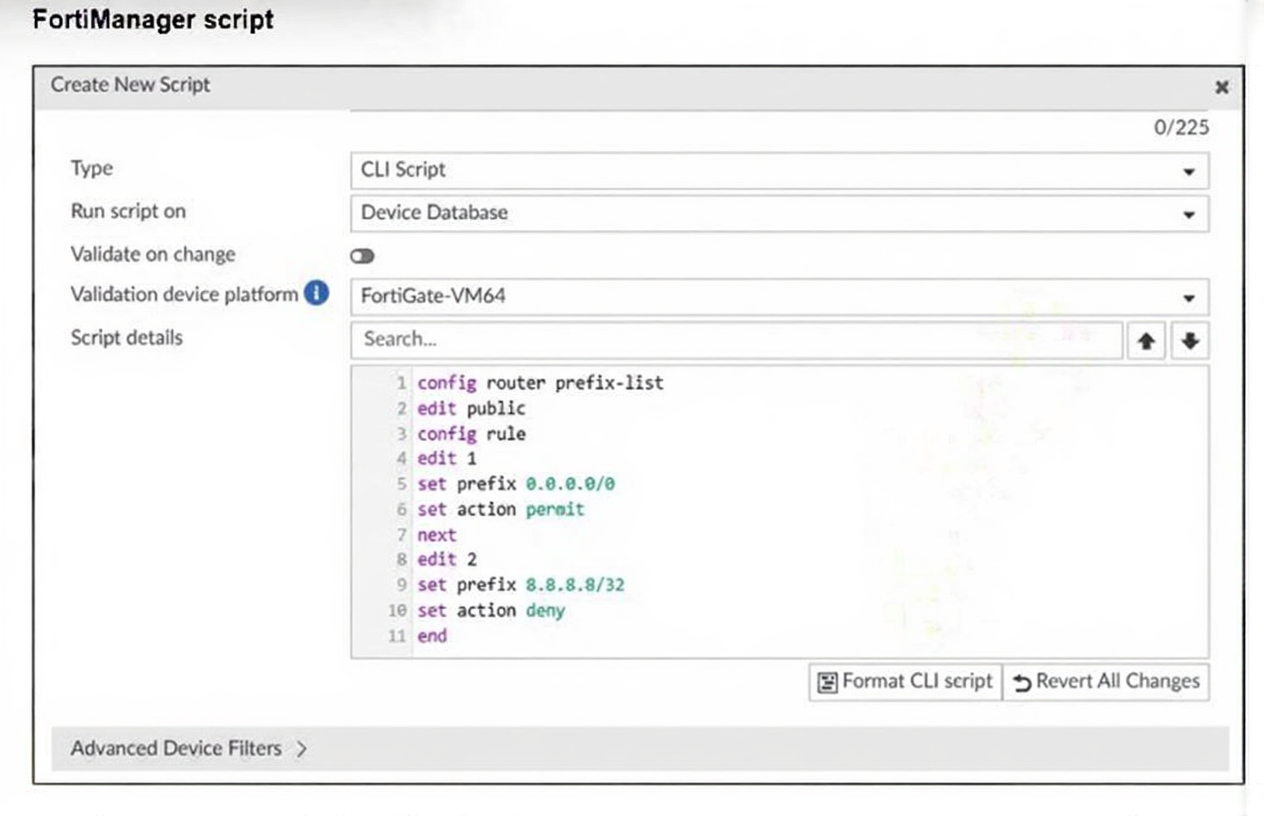
Which two results occur if you run the script using theDevice Databaseoption? (Choose two.)
A. The device Config Status is tagged as Modified.
B. The script history shows the successful installation of the script on the remote FortiGate.
C. The successful execution of a script on the Device Database creates a new revision history.
D. The administrator must install these changes on a managed device using the Install Wizard.
Explanation:
✅Why A is correct
When a script is executed on the Device Database, it modifies the configuration stored locally on FortiManager, not on the actual FortiGate.
This causes FortiManager to flag the device’s Config Status as “Modified”, indicating that the local config differs from the device’s actual running config.
This is a key operational signal that an install action is pending.
✅ Why D is correct
Since the script only updates the Device Database, the changes are not yet pushed to the FortiGate.
To apply the changes, the administrator must use the Install Wizard to deploy the updated config to the managed device.
This is standard FortiManager workflow: Device Database → Install Wizard → FortiGate.
❌ Why B is wrong
The script history only logs executions on the actual device, not on the Device Database.
Running the script on the Device Database does not trigger remote execution, so no history entry is created for the FortiGate.
❌ Why C is wrong
ADOM revision history is only updated when you manually create a revision or install a policy package.
Running a script on the Device Database does not automatically create a revision.
📖 Reference
FortiManager 7.6 Admin Guide – “Scripts run on the Device Database modify the local configuration. These changes must be installed to the device using the Install Wizard.”
| Page 1 out of 6 Pages |
| 123 |
Choosing the right preparation material is critical for passing the Fortinet FortiManager 7.6 Administrator exam. Here’s how our FCP_FMG_AD-7.6 practice test is designed to bridge the gap between knowledge and a passing score.