Last Updated On : 3-Mar-2026
Total 40 Questions
The smartest way to prepare for your Fortinet FCSS_LED_AR-7.6 exam isn't just reading—it's practicing. Our Fortinet NSE 6 LAN Edge 7.6 Architect practice test bridge gap, transforming your knowledge into a passing score. Familiarize yourself with the exact style and difficulty of the real Fortinet FCSS_LED_AR-7.6 practice questions, so there are no surprises. Get detailed feedback to identify your strengths and target your weaknesses, making your study time more efficient.
High Availability and Redundancy
Refer to the exhibit.
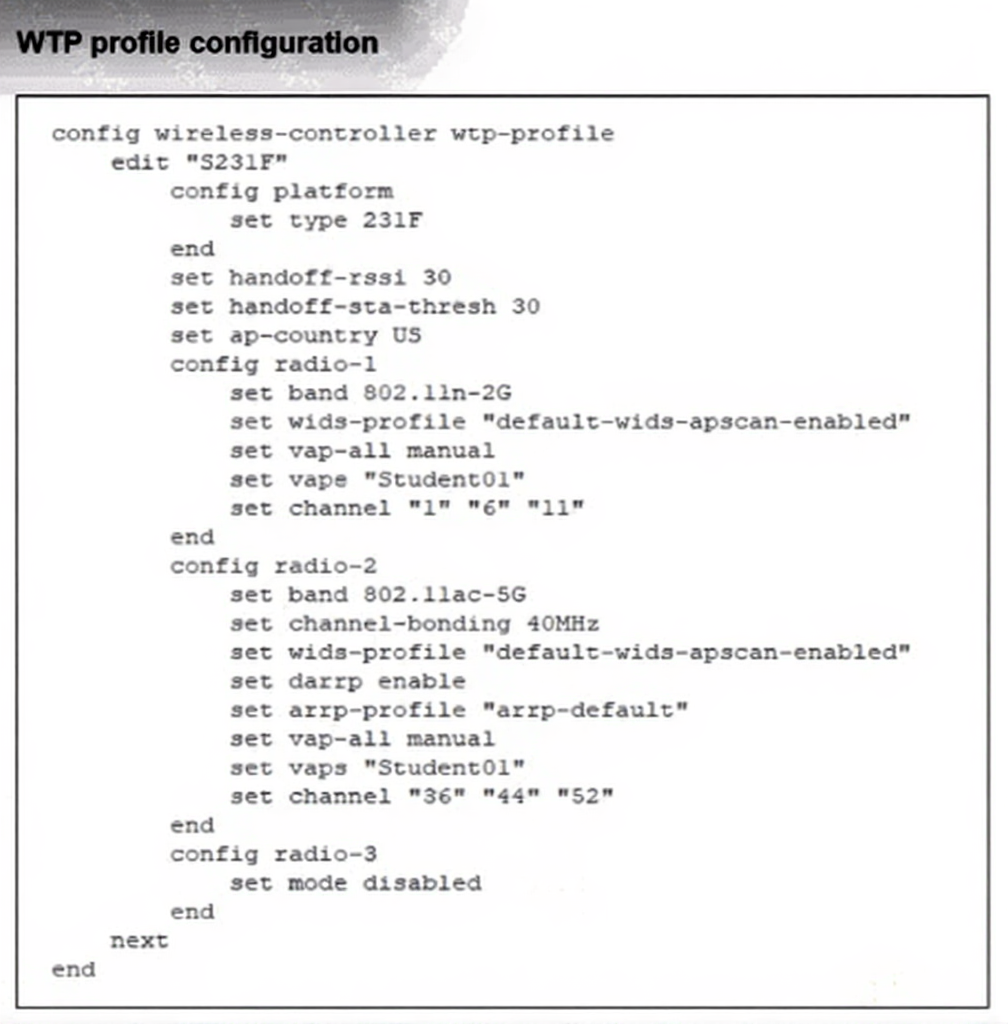
Which shows the WTP profile configuration.
The AP profile is assigned to two FAP-231F APs that are installed in an open plan area.
The first AP has 32 clients associated with the 5 GHz radios and 22 clients associated with the 2.4 GHz radio.
The second AP has 12 clients associated with the 5 GHz radios and 20 clients associated with the 2.4 GHz
radio.
A dual-band-capable client enters the area near the first AP and the first AP measures the new client at - 3 3
dBm signal strength. The second AP measures the new client at -43 dBm signal strength.
If the new client attempts to conned to the student 01 wireless network, which AP radio will the client be
associated with?
A. The first AP 2.4 GHz interface provides a stronger signal, which clients often prioritize.
B. The first AP 5 GHz interface because it has a stronger signal.
C. The second AP 5 GHz interface has fewer clients, which ensures better performance despite the weaker signal.
D. The second AP 2.4 GHz interface is preferred over 5 GHz for better speed and lower interference.
Explanation:
Why the correct answer is right
Fortinet's Frequency Handoff (also called band steering) is designed exactly for this scenario: it pushes dual-band clients toward the 5 GHz band whenever the signal is strong enough to deliver better performance (faster speeds, less interference).
In the WTP profile, set handoff-rssi 30 means the controller checks the client's RSSI on 5 GHz — if it's better than (stronger than) -30 dBm (remember, -33 dBm is stronger than -30 dBm because lower negative numbers = better signal), the AP ignores probe requests on 2.4 GHz from that client and forces association on 5 GHz. Here, the client is very close to the first AP (-33 dBm is excellent), so Frequency Handoff kicks in hard. The client ends up on the first AP's 5 GHz radio for optimal throughput.
Why option A is wrong
This assumes clients naturally "prioritize" 2.4 GHz for stronger signals — but that's not how it works in Fortinet setups with Frequency Handoff enabled. The controller actively suppresses 2.4 GHz associations for dual-band clients when 5 GHz RSSI exceeds the handoff-rssi threshold. Even if 2.4 GHz might appear stronger in some edge cases, the policy overrides client preference to favor 5 GHz when conditions are met (which they clearly are at -33 dBm).
Why option C is wrong
Load balancing between APs (via AP Handoff) does consider client counts (handoff-sta-thresh 30), and the first AP's 5 GHz is at exactly 32 clients (right at the threshold). However, AP Handoff only moves clients if there's a nearby AP with sufficient RSSI (again tied to handoff-rssi). The second AP's signal is -43 dBm — noticeably weaker and likely below effective handoff thresholds in practice. The controller prioritizes strong signal over slight load differences, so no handoff to the distant second AP occurs.
Why option D is wrong
This reverses reality: 5 GHz almost always provides higher speeds (thanks to wider channels and less crowding) compared to 2.4 GHz, which has better range but more interference and lower max throughput. Fortinet's Frequency Handoff exists to steer capable clients away from 2.4 GHz toward 5 GHz — never the other way around for "better speed." This option completely contradicts the purpose of the feature.
Official Fortinet References:
Wireless client load balancing for high-density deployments (FortiAP / FortiWiFi 7.6.x) → Explains Frequency Handoff logic, how the AP ignores 2.4 GHz probes when 5 GHz RSSI > handoff-rssi threshold, and client association decisions.
https://docs.fortinet.com/document/fortiap/7.6.3/fortiwifi-and-fortiap-configuration-guide/538473/wireless-client-load-balancing-for-high-density-deployments
CLI reference for config wireless-controller wtp-profile (handoff-rssi definition) → Confirms handoff-rssi sets the 5 GHz RSSI threshold (range 20–30) for forcing band steering.
https://docs.fortinet.com/document/fortigate/7.6.0/cli-reference (search for "handoff-rssi" in wtp-profile section)
Refer to the exhibit.
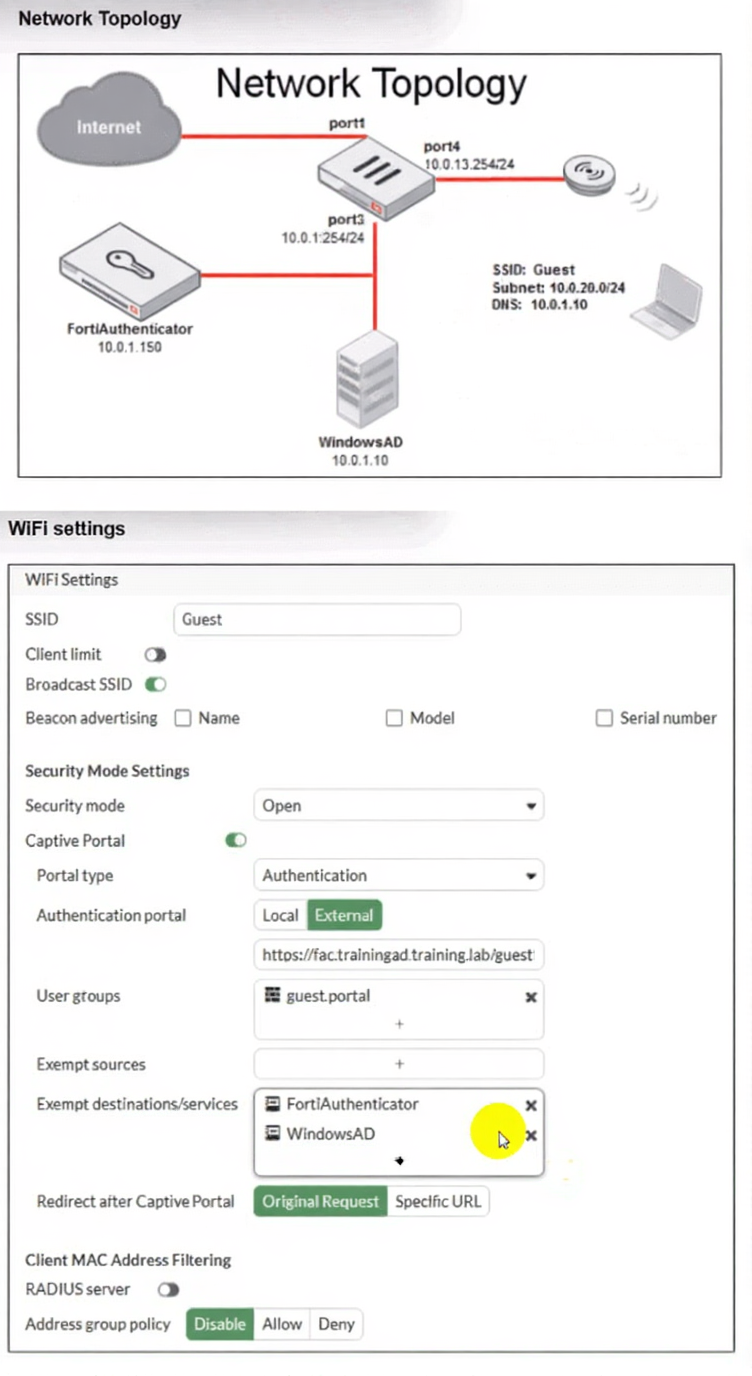
Review the exhibits to analyze the network topology, SSID settings, and firewall policies.
FortiGate is configured to use an external captive portal for authentication to grant access to a wireless
network. During testing, it was found that users attempting to connect to the SSID cannot access the captive
portal login page.
What configuration change should be made to resolve this issue to allow users to access the captive portal?
A. Change the SSID security mode to WPA2-Enterprise for authentication.
B. Disable HTTPS redirection for the captive portal authentication page.
C. Exclude FortiAuthenticator and Windows AD address objects from filtering.
D. A firewall policy allowing Guest SSID traffic to reach FortiAuthenticator and Windows AD.
Explanation
The problem is a connectivity issue, not an authentication protocol issue. Users on the Guest SSID (10.0.20.0/24) cannot load the captive portal page hosted externally. For the initial portal page load and subsequent authentication to work, clients must be able to reach the FortiAuthenticator (10.0.1.150) and the Windows AD/DNS server (10.0.1.10). Firewall policies in FortiGate are interface-based and control traffic flow between networks.
✅ Why Option D is Correct
The Guest SSID resides on its own subnet (10.0.20.0/24). By default, traffic between different interfaces/subnets on a FortiGate is blocked unless a firewall policy explicitly allows it.
To reach the captive portal server (FortiAuthenticator at 10.0.1.150) and the DNS server (Windows AD at 10.0.1.10), which are on a different subnet (10.0.1.0/24), a firewall policy must exist permitting traffic from the Guest SSID interface (or its source IP range) to the internal network interface where these servers reside.
The current topology does not show such a policy. Creating this policy is the fundamental requirement to establish the initial network path for the captive portal to function.
❌ Why the Other Options Are Wrong
A. Change the SSID security mode to WPA2-Enterprise for authentication.
Why it's wrong: The issue is that users cannot access the login page at all. This is a network reachability problem that occurs before any WPA or 802.1X authentication takes place. Changing the security mode does not solve the underlying routing/firewall block.
B. Disable HTTPS redirection for the captive portal authentication page.
Why it's wrong: While HTTPS redirection can sometimes cause issues if certificates are misconfigured, the core problem described is a complete failure to load the page. The exhibit shows the portal URL is https://.... If the client cannot even route a packet to the server, the protocol (HTTP vs. HTTPS) is irrelevant. The primary barrier is a missing firewall rule.
C. Exclude FortiAuthenticator and Windows AD address objects from filtering.
Why it's wrong: This is a misapplication of a feature. The "Exempt destinations" field in the captive portal configuration is for allowing client access to specific resources (like update servers) before they authenticate. It does not create the necessary firewall policy for clients to reach the authentication servers themselves in the first place. The traffic to the auth servers for the purpose of loading the portal and processing credentials still needs a firewall policy.
📚 Official References
FortiOS Handbook - Captive Portals: The documentation emphasizes that for external captive portals, the FortiGate must be able to communicate with the external portal server, and clients must have network access to it.
FortiAuthenticator Administration Guide - Captive Portal: Details the network requirements for integrating FortiAuthenticator as an external portal server.
Firewall Policy Concept: The principle that inter-VLAN/interface traffic requires an explicit firewall policy is a core tenet of FortiGate operation.
When troubleshooting a captive portal issue, which POST parameter in the redirected HTTPS request can be used to track the user's session and ensure that the request is valid?
A. username
B. redir
C. magic
D. email
Explanation
✅ C. magic
This parameter is a session-specific token generated by the FortiGate.
It validates that the HTTPS POST request belongs to the original captive portal redirection.
FortiGate uses magic to bind the user, IP, and session together.
If magic is missing or incorrect, authentication fails immediately, even if credentials are correct.
❌ A. username
Only carries the user’s login name.
Provides no session validation.
Cannot prevent replay or forged authentication attempts.
❌ B. redir
Used solely for post-authentication redirection.
Does not identify or validate the client session.
Irrelevant for troubleshooting session legitimacy.
❌ D. email
Optional user-provided data.
Not required by FortiGate for authentication.
Has zero role in session tracking or request validation.
Key Exam Rule
If the question mentions session tracking, request validation, or external captive portal troubleshooting, the answer is magic.
Official Fortinet Reference
FortiGate Captive Portal – External Authentication (7.6)
https://docs.fortinet.com/document/fortigate/7.6.0/captive-portal/921668/external-captive-portal
You are troubleshooting a Syslog-based single sign-on (SSO) issue on FortiAuthenticator, where user authentication is not being correctly mapped from the syslog messages. You need a tool to diagnose the issue and understand the logs to resolve it quickly. Which tool in FortiAuthenticator can you use to troubleshoot and diagnose a Syslog SSO issue?
A. Debug logs > Remote Servers > Syslog Viewer
B. Parsing Test Tool
C. Debug logs > SSO Sessions page
D. Debug logs > Single Sign-On > Syslog SSO
Explanation
The Parsing Test Tool provides real-time validation of syslog parsing rules, showing exactly how FortiAuthenticator extracts usernames and IP addresses from syslog messages to diagnose SSO mapping failures.
Why Option B is Correct
Located at Fortinet SSO > SSO > Syslog Sources > Parsing Test, this tool lets administrators paste actual syslog messages to test parsing rules immediately. It displays matched groups, extracted usernames, and IP mappings without impacting live SSO processing—perfect for pinpointing regex pattern issues causing authentication failures.
Why Other Options Are Wrong
A. Debug logs > Remote Servers > Syslog Viewer ❌:
This tool displays raw syslog messages received by FortiAuthenticator from network devices but provides no parsing analysis, regex testing, or username/IP extraction validation. Users see unparsed log entries without understanding why SSO mappings fail.
C. Debug logs > SSO Sessions page ❌:
Shows only successfully authenticated SSO sessions after parsing completes. When syslog parsing fails initially, no sessions appear here, making it useless for diagnosing upstream parsing configuration problems.
D. Debug logs > Single Sign-On > Syslog SSO ❌:
Generic debug logging zone that captures broad SSO events but lacks the specific parsing rule testing functionality needed to validate syslog message format interpretation in real-time.
Official References
FortiAuthenticator Syslog SSO Guide:
https://docs.fortinet.com/document/fortiauthenticator/6.6.0/administration-guide/713528/syslog-sources
FAC Troubleshooting Tools:
https://community.fortinet.com/t5/FortiAuthenticator/Troubleshooting-Tip-Basic-FortiAuthenticator-troubleshooting/ta-p/337001
A FortiSwitch is not appearing in the FortiGate management interface after being connected via FortiLink. What could be a first troubleshooting step?
A. Ensure that the FortiGate security policies allow traffic from the FortiSwitch.
B. Manually assign a static IP to the FortiSwitch.
C. Verify that FortiGate device DHCP server is assigning an IP to the FortiSwitch.
D. Ensure the FortiSwitch has internet access.
Explanation
For a FortiGate to manage a FortiSwitch, the FortiLink handshake must occur. A factory-reset FortiSwitch automatically sends DHCP requests on its uplink ports to find a controller.
The FortiGate must have a DHCP Server enabled on the FortiLink interface to assign the switch an IP address. Beyond basic networking, this DHCP offer includes Option 138 (CAPWAP) or proprietary messaging that informs the switch of the FortiGate's management IP. Without an IP address, the switch cannot establish the management tunnel, leaving it invisible in the "Managed FortiSwitches" list.
Why Option C is Correct
C. Verify that FortiGate device DHCP server is assigning an IP to the FortiSwitch. ✅
This is the essential starting point for troubleshooting. Connectivity is impossible without a Layer 3 address. If the DHCP monitor shows no lease for the switch's MAC address, the FortiLink interface on the FortiGate is likely missing a DHCP server, the pool is exhausted, or the physical cabling is not on a discovery-enabled port.
Why Other Options are Wrong
A. Ensure that the FortiGate security policies allow traffic... ❌
Management traffic between the FortiGate and FortiSwitch is local-in traffic. It is handled by the internal switch-controller process and does not require a firewall policy to appear in the management interface.
B. Manually assign a static IP to the FortiSwitch. ❌
Manual IP assignment is counter-intuitive to the Zero-Touch Provisioning (ZTP) model of FortiLink. While possible in complex Layer 3 setups, it is not a standard "first step" for basic discovery issues.
D. Ensure the FortiSwitch has internet access. ❌
FortiLink management is strictly local. A switch does not need to reach the internet to be discovered or managed by its local FortiGate controller.
Official Reference Links
FortiSwitch 7.6.0 FortiLink Guide - Configuring FortiLink
Fortinet KB: Troubleshooting FortiSwitch Discovery
Which FortiGuard licenses are required for FortiLink device detection to enable device identification and vulnerability detection?
A. FortiGuard Vulnerability Management and FortiGuard Endpoit Protection
B. FortiGuard Threat Intelligence and FortiGuard loT Detection
C. FortiGuard Threat Intelligence and FortiGuard Endpoint Protection
D. FortiGuard Attack Surface Security and FortiGuard loT Detection
Explanation
✅ B. FortiGuard Threat Intelligence and FortiGuard IoT Detection
This is the correct answer because FortiLink device detection relies on passive fingerprinting and threat context rather than endpoint agents or active scanning. FortiGuard IoT Detection is responsible for identifying connected devices by type, vendor, operating system, and behavior, including unmanaged and IoT devices connected through FortiSwitch. FortiGuard Threat Intelligence complements this by enriching the detected devices with known threat and vulnerability context. Without these two licenses together, FortiGate cannot fully identify devices or assess their risk level through FortiLink.
❌ A. FortiGuard Vulnerability Management and FortiGuard Endpoint Protection
This option is incorrect because Vulnerability Management focuses on infrastructure and asset scanning, not passive device detection through FortiLink. Endpoint Protection applies only to endpoints managed by FortiClient and does not identify unmanaged or IoT devices, which are the primary targets of FortiLink device detection.
❌ C. FortiGuard Threat Intelligence and FortiGuard Endpoint Protection
Although Threat Intelligence is required, Endpoint Protection does not contribute to device fingerprinting or vulnerability detection for devices connected via FortiLink. Without FortiGuard IoT Detection, FortiGate cannot identify device types or behaviors, making this license combination insufficient.
❌ D. FortiGuard Attack Surface Security and FortiGuard IoT Detection
While IoT Detection is relevant, Attack Surface Security is designed to monitor internet-facing assets and external exposure. It does not integrate with internal FortiLink device discovery or contribute to device identification within the LAN.
Official Fortinet References
FortiGuard IoT Detection Overview:
https://www.fortinet.com/products/fortiguard/fortiguard-iot-security
FortiGate 7.6 Administration Guide – Device Detection:
https://docs.fortinet.com/document/fortigate/7.6.0/administration-guide/648508/device-detection
Refer to the exhibits.
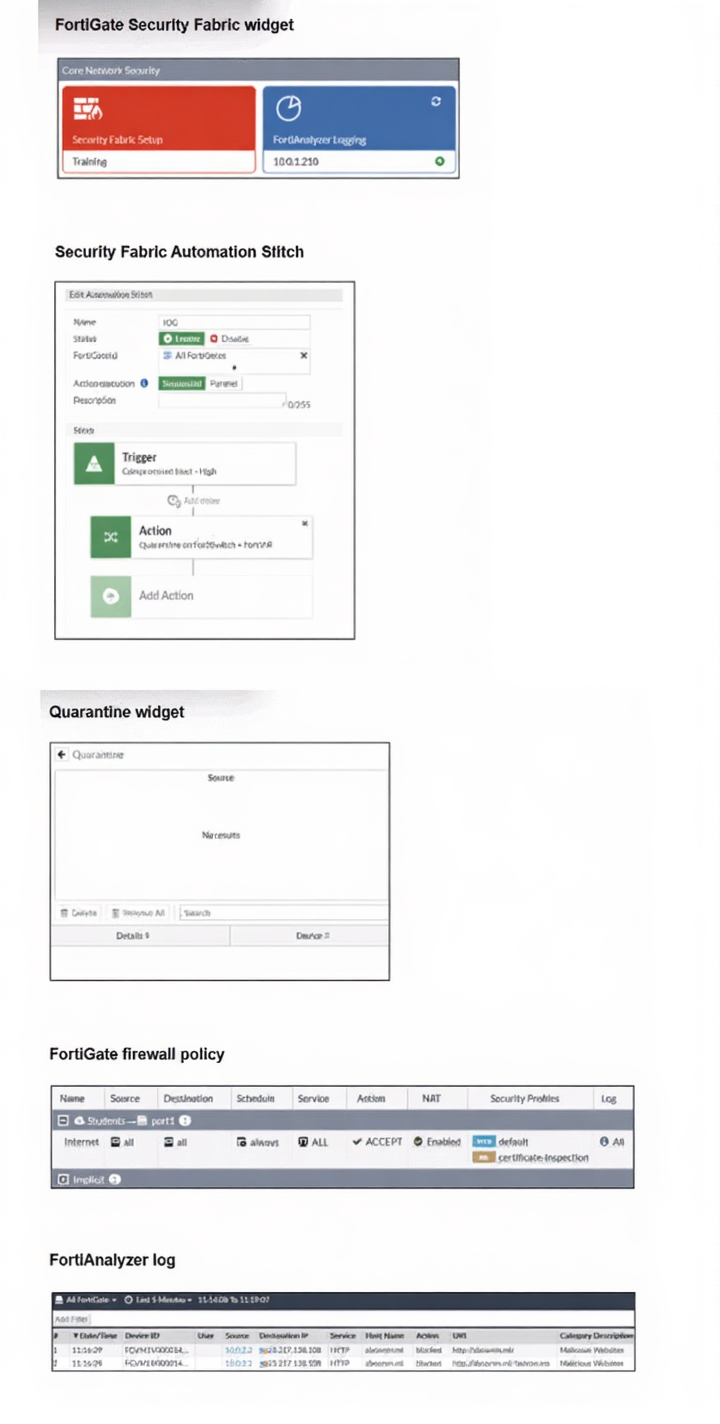
Examine the FortiGate configuration, FortiAnalyzer logs, and FortiGate widget shown in the exhibits.
Security Fabhc quarantine automation has been configured to isolate compromised devices automatically.
FortiAnalyzer has been added to the Security Fabric, and an automation stitch has been configured to
quarantine compromised devices.
To test the setup, a device with the IP address 10.0.2.1 that is connected through a managed FortiSwitch
attempts to access a malicious website. The logs on FortiAnalyzer confirm that the event was recorded, but
the device does not appear in the FortiGate quarantine widget.
Which two reasons could explain why FortiGate is not quarantining the device? (Choose two.)
A. The IOC action should include only the FortiSwitch in the quarantine.
B. The SSL inspection should be set to deep-Inspection
C. The malicious website is not recognized as an indicator of compromise (IOC) by FortiAnalyzer.
D. The threat detection services license is missing or invalid under FortiAnalyzer.
Explanation
For FortiAnalyzer-driven quarantine, the system must classify a log as a high-confidence threat. Even if a log exists, the automation stitch only triggers if FortiAnalyzer identifies it as an Indicator of Compromise (IOC). If the IOC feature is unlicensed or the specific threat isn't in the IOC database, the event handler won't fire, and the FortiGate will not execute the quarantine action.
Why These Options are Correct
C. The malicious website is not recognized as an indicator of compromise (IOC) by FortiAnalyzer. ✅
The automation stitch is tied to the FortiAnalyzer Event Handler. If the traffic log isn't flagged as an IOC, the handler ignores it. Without that "Compromised Host" tag, the FortiGate never receives the instruction to isolate the device.
D. The threat detection services license is missing or invalid under FortiAnalyzer. ✅
The IOC engine requires a valid FortiGuard Threat Detection Service subscription. Without this license, FortiAnalyzer cannot correlate logs against the global threat database, meaning no IOCs are generated to trigger the automation stitch.
Why Other Options are Wrong
A. The IOC action should include only the FortiSwitch in the quarantine. ❌
Quarantine is a coordinated Security Fabric action. The FortiGate issues the command, and the managed FortiSwitch enforces it. Restricting the configuration "only to the switch" is not a valid troubleshooting step for a failure to trigger.
B. The SSL inspection should be set to deep-inspection. ❌
Since the logs already exist in FortiAnalyzer, the FortiGate has already successfully identified the malicious traffic. Deep inspection might help detect more threats, but it isn't the reason a previously detected threat failed to trigger an automation stitch.
Official Reference Links
FortiAnalyzer 7.6 Administration Guide - Indicators of Compromise
FortiGate 7.6 Administration Guide - Automation Stitches
| Page 1 out of 6 Pages |
| 123 |
Choosing the right preparation material is critical for passing the Fortinet NSE 6 LAN Edge 7.6 Architect exam. Here’s how our FCSS_LED_AR-7.6 practice test is designed to bridge the gap between knowledge and a passing score.