Last Updated On : 3-Mar-2026
Total 81 Questions
The smartest way to prepare for your Fortinet NSE7_SSE_AD-25 exam isn't just reading—it's practicing. Our Fortinet NSE 7 FortiSASE 25 Enterprise Administrator practice test bridge gap, transforming your knowledge into a passing score. Familiarize yourself with the exact style and difficulty of the real Fortinet NSE7_SSE_AD-25 practice questions, so there are no surprises. Get detailed feedback to identify your strengths and target your weaknesses, making your study time more efficient.
What action must a FortiSASE customer take to restrict organization SaaS access to only FortiSASEconnected users? (Choose one answer)
A. Implement a CNAPP solution to allowlist the users under the FortiSASE egress IP
B. Implement ZTNA for their private apps and allow list them under SaaS portals or grant them conditional access.
C. Connect FortiSASE to an SPA hub for private access to an allowlisted connecting IP.
D. Retrieve the PoPs of the users' public IP addresses from the FortiSASE region IP list and whitelist the IP under SaaS portals, or grant them conditional access.
Explanation:
FortiSASE customers need to restrict SaaS access to only users connected through FortiSASE PoPs to ensure secure egress traffic. This prevents unauthorized access from non-corporate IPs while maintaining granular control over SaaS applications. The correct method leverages FortiSASE's regional IP lists containing PoP public IPs, which SaaS providers can whitelist for conditional access.
✅ Correct Answer: D
Retrieving FortiSASE PoPs' public IP addresses from the region IP list allows customers to whitelist these specific egress IPs in SaaS portals like Microsoft 365 or Google Workspace. This ensures only traffic originating from FortiSASE-connected users gains access, enforcing zero-trust principles. SaaS providers support conditional access policies based on trusted IP ranges, making this the standard implementation for FortiSASE SaaS security.
❌ Incorrect answer: A
CNAPP solutions focus on cloud-native application protection and workload security, not user IP allowlisting for SaaS access. They lack integration with FortiSASE PoP egress IPs and cannot dynamically manage regional IP lists for SaaS conditional access policies. This approach adds unnecessary complexity without addressing the core requirement of IP-based egress control.
❌ Incorrect answer: B
ZTNA secures private application access, not public SaaS services, and allowlisting private apps under SaaS portals is not feasible since SaaS operates via public endpoints. Conditional access in SaaS targets user identity or IP, not ZTNA tunnels, making this mismatched for FortiSASE SaaS restrictions.
❌ Incorrect answer: C
SPA (Secure Private Access) hubs manage private app connectivity via tunnels, not public SaaS access which uses direct internet egress. Allowlisting SPA hub IPs won't restrict SaaS traffic since users connect to SaaS via FortiSASE PoPs, not SPA infrastructure.
Reference:
Fortinet official documentation - FortiSASE Secure SaaS Access guides
What are two benefits of deploying secure private access (SPA) with SD-WAN? (Choose two answers)
A. ZTNA posture check performed by the hub FortiGate
B. Support of both TCP and UDP applications
C. A direct access proxy tunnel from FortiClient to the on-premises FortiGate
D. Inline security inspection by FortiSASE
Explanation:
Deploying Secure Private Access (SPA) with SD-WAN in FortiSASE gives remote users secure, high-performance access to on-premises applications. The two key benefits are full support for both TCP and UDP protocols (critical for legacy and real-time apps) and consistent inline security inspection applied by FortiSASE cloud PoPs before traffic reaches private resources. These advantages come directly from using SD-WAN overlays with FortiSASE PoPs acting as dynamic spokes.
✅ Correct Answer: B. Support of both TCP and UDP applications
Fortinet explicitly states in the FortiSASE Architecture Guide that the SPA with SD-WAN deployment model provides “broader and seamless access to privately hosted TCP- and UDP-based applications.” Because it uses IPsec tunnels and ADVPN dynamic shortcuts, it avoids the TCP-only limitation of some proxy-based tunnels. This is essential for organizations that still use UDP-based applications such as VoIP, video conferencing, legacy systems, or custom protocols. This is one of the main reasons Fortinet recommends this model.
✅ Correct Answer: D. Inline security inspection by FortiSASE
In the SPA with SD-WAN topology, all remote user traffic first enters a FortiSASE Point of Presence (PoP). FortiSASE applies its full cloud-delivered security stack — including NGFW, IPS, web filtering, anti-malware — inline before forwarding the traffic through SD-WAN tunnels to on-premises resources. This gives consistent SSE protection for private app access without relying only on on-premises inspection. This is clearly listed as a major benefit in official documentation.
❌ Incorrect answer: A. ZTNA posture check performed by the hub FortiGate
While the hub FortiGate does apply access policies, Fortinet documentation explains that ZTNA posture checks (device compliance, certificate validation, etc.) are primarily enforced by FortiClient and the FortiSASE PoP before the tunnel is established. The hub FortiGate focuses on routing, BGP, and policy enforcement after the connection is already allowed. Therefore, saying the posture check is “performed by the hub FortiGate” is not accurate for this deployment model.
❌ Incorrect answer: C. A direct access proxy tunnel from FortiClient to the on-premises FortiGate
This is not correct. In SPA with SD-WAN, FortiClient never connects directly to the on-premises FortiGate. Traffic always goes first to the nearest FortiSASE PoP (which acts as a spoke), and only then does the PoP create IPsec tunnels (with possible ADVPN shortcuts) to the organization’s SD-WAN hubs. The word “direct” is misleading — the PoP is always in the middle. This description fits other SPA modes, not the SD-WAN integrated model.
Reference:
Only official Fortinet sources:
🔹 FortiSASE Architecture Guide → “SPA using SD-WAN” section
🔹 Fortinet Document Library → Secure Private Access (SPA) deployment with SD-WAN
Which statement about FortiSASE and SAML is true? (Choose one answer)
A. FortiSASE acts as the SP, relies on an external IdP, and can use SAML group matching.
B. FortiSASE supports SAML login but cannot use SAML group matching.
C. FortiSASE acts as the IdP and can perform SAML group matching internally.
D. FortiSASE includes IdP functionality and uses it for SAML group matching.
Explanation:
This question tests how FortiSASE integrates with SAML for user authentication and authorization. Specifically, it focuses on FortiSASE’s role in the SAML trust model and whether it can consume group or attribute information from an external Identity Provider. Understanding this is critical for policy enforcement, as FortiSASE relies on identity attributes provided by third-party IdPs rather than acting as an identity authority itself.
✅ Correct Answer: A
FortiSASE operates strictly as a SAML Service Provider (SP) and depends on an external Identity Provider (IdP) such as Azure AD, Okta, or FortiAuthenticator for authentication. During SAML assertion exchange, FortiSASE can consume attributes like group membership and use SAML group matching to apply access policies. This is the supported and documented design for identity-based access in FortiSASE.
❌ Incorrect Answer: B
This option is incorrect because FortiSASE does support SAML group matching. Group or attribute values sent by the IdP in the SAML assertion can be mapped to FortiSASE user groups and used in policy rules. Claiming that FortiSASE cannot use group matching ignores a core feature required for identity-aware SSE enforcement and contradicts Fortinet’s configuration guides.
❌ Incorrect Answer: C
This statement is false because FortiSASE does not act as a SAML Identity Provider. It cannot authenticate users directly or generate SAML assertions. All authentication must be handled by an external IdP. Since FortiSASE is not an IdP, it cannot perform internal SAML group matching independent of an external identity source.
❌ Incorrect Answer: D
FortiSASE does not include built-in IdP functionality for SAML. While Fortinet products like FortiAuthenticator can function as an IdP, FortiSASE itself is limited to the SP role. Therefore, it cannot originate SAML authentication or manage identities internally, making this statement architecturally incorrect.
Reference
Fortinet FortiSASE Administration Guide
Fortinet FortiSASE Identity and Access Management Documentation
Fortinet SAML Authentication Technical Documentation
What are the key differences between the FortiSASE BGP per overlay and BGP on loopback routing design methods? (Choose one answer)
A. BGP per overlay can use separate iBGP sessions for each spoke-to-hub tunnel with mode-cfg enabled for IP address assignment, while BGP on loopback uses a single iBGP session per hub terminating on a loopback interface to simplify configuration and reduce advertised routes.
B. BGP per overlay establishes a single iBGP session per hub on a loopback interface, while BGP on loopback requires mode-cfg for IP address assignment and uses multiple iBGP sessions per tunnel.
C. BGP per overlay is used for loopback interfaces to reduce routes, while BGP on loopback is the default method requiring separate iBGP sessions for each spoke.
D. BGP per overlay simplifies hub configuration without mode-cfg, while BGP on loopback establishes multiple iBGP sessions for each tunnel to increase advertised routes.
Explanation:
This question focuses on two BGP routing design methods available in FortiSASE SD-WAN architecture. The key distinction lies in how iBGP sessions are established between hubs and spokes, affecting configuration complexity, IP assignment mechanisms, and route advertisement scale.
✅ Correct Answer:
A. BGP per overlay can use separate iBGP sessions for each spoke-to-hub tunnel with mode-cfg enabled for IP address assignment, while BGP on loopback uses a single iBGP session per hub terminating on a loopback interface to simplify configuration and reduce advertised routes.
This answer correctly identifies the core operational difference. In the BGP per overlay design, each individual IPSec or GRE tunnel between a spoke and a hub requires its own iBGP session. The mode-cfg (mode config) is often used in this scenario to dynamically assign the tunnel IP address to the spoke from the hub. In contrast, the BGP on loopback method consolidates routing. The spoke establishes a single iBGP session to a loopback interface IP on the hub, which is reachable via all the overlay tunnels (using recursive routing). This simplifies the hub BGP configuration significantly and reduces the number of routes the hub advertises, as it advertises a summary loopback route instead of individual tunnel networks.
❌ Incorrect Answers:
B. BGP per overlay establishes a single iBGP session per hub on a loopback interface, while BGP on loopback requires mode-cfg for IP address assignment and uses multiple iBGP sessions per tunnel.
This option completely reverses the definitions. It incorrectly assigns the "single iBGP session on a loopback" characteristic to BGP per overlay and the "multiple sessions" characteristic to BGP on loopback, which is the opposite of their true functionality.
C. BGP per overlay is used for loopback interfaces to reduce routes, while BGP on loopback is the default method requiring separate iBGP sessions for each spoke.
This option incorrectly swaps the primary purposes. The method specifically associated with using a loopback interface to reduce routes is BGP on loopback, not BGP per overlay. It also incorrectly labels BGP on loopback as the default requiring multiple sessions.
D. BGP per overlay simplifies hub configuration without mode-cfg, while BGP on loopback establishes multiple iBGP sessions for each tunnel to increase advertised routes.
This option is incorrect on multiple points. BGP per overlay generally complicates hub configuration due to multiple sessions and often uses mode-cfg. BGP on loopback is the design that simplifies configuration and aims to reduce advertised routes, not increase them.
Reference:
Fortinet Documentation Library: FortiSASE Administration Guide, specifically the SD-WAN Overlay Routing sections comparing "BGP per overlay" and "BGP on loopback interface" design methodologies.
Refer to the exhibit.
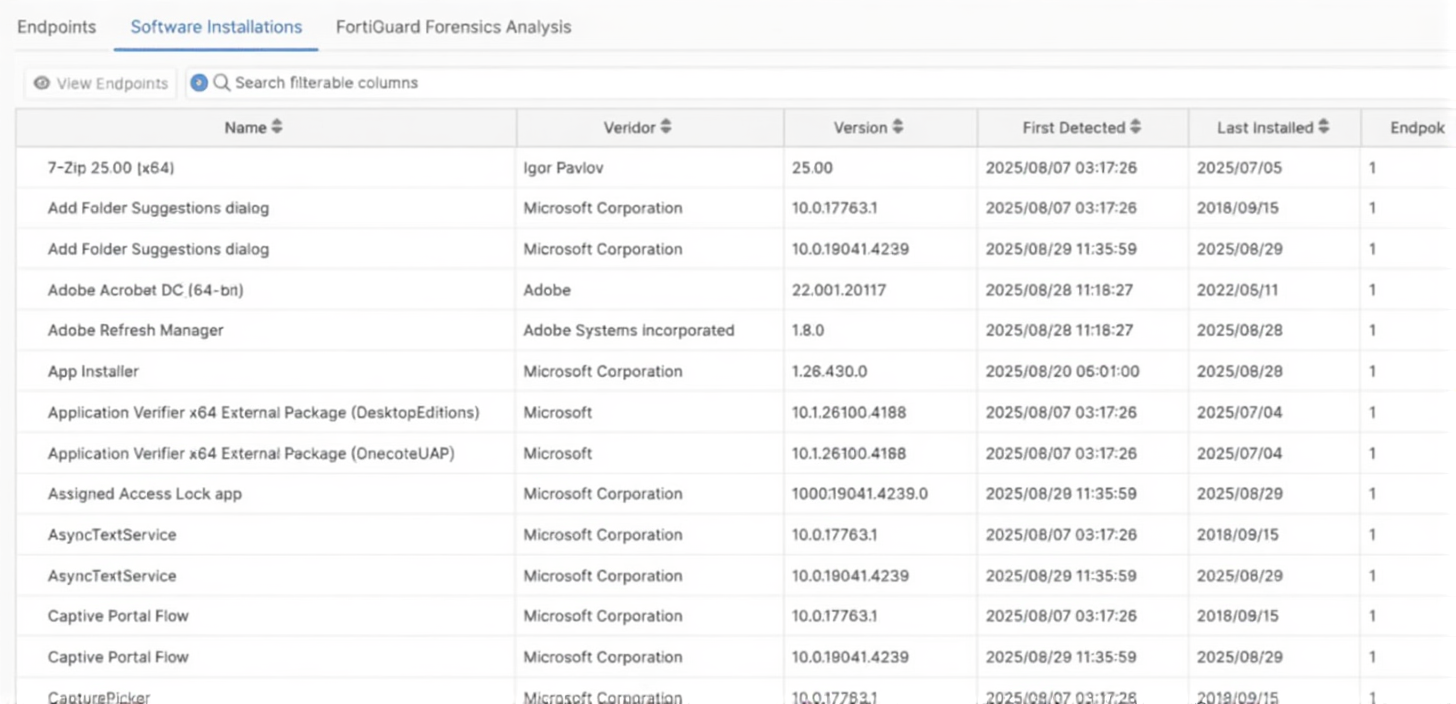
Which type of information or actions are available to a FortiSASE administrator from the following output?
(Choose one answer)
A. Administrators can view and configure endpoint profiles and ZTNA tags.
B. Administrators can view and configure automatic patching of endpoints, and first detected date for applications.
C. Administrators can view latest application version available and push updates to managed endpoints.
D. Administrators can view application details, such as vendor, version, and installation dates to identify unwanted or outdated software.
Explanation:
The exhibit displays the Software Installations tab under the Endpoints menu in the FortiSASE dashboard. This view provides a centralized inventory of all software detected on managed endpoints, including details like the vendor, version, and the date it was first detected or installed. This visibility is crucial for administrators to maintain compliance, perform security audits, and identify potentially unauthorized or vulnerable software within the organization's environment.
✅ Correct Answer:
Option D: In the FortiSASE Software Installations pane, administrators can monitor a comprehensive list of all applications installed on devices registered with FortiClient. By reviewing columns like Vendor, Version, and Last Installed, administrators gain the necessary visibility to detect outdated software versions that might pose security risks or identify unwanted applications that violate corporate policy. This granular data helps in maintaining a secure and standardized endpoint environment across the remote workforce.
❌ Incorrect Answers:
Option A: While FortiSASE does allow the configuration of endpoint profiles and ZTNA tags, these actions are performed under the Configuration > Endpoint Management or ZTNA Tagging menus. The exhibit specifically shows the "Software Installations" view, which is a reporting and monitoring tool rather than a configuration interface for policy-based ZTNA tags or profile assignments.
Option B: Although the output correctly displays the "First Detected" date for applications, FortiSASE does not directly handle the automatic patching of third-party software from this specific dashboard view. Patch management is typically a function of a dedicated UEM or the FortiClient EMS Vulnerability Scan module. This view is primarily for visibility and inventory purposes rather than active remediation or patching orchestration.
Option C: The exhibit shows the version of the software currently installed on the endpoint, but it does not display the "latest application version available" in the global market. Furthermore, FortiSASE's Software Installations tab is a passive inventory tool; it does not provide a mechanism to "push updates" or deploy software packages directly to managed endpoints from this specific list.
Reference:
Official Fortinet Documentation: FortiSASE - Endpoints - Software Installations
For monitoring potentially unwanted applications on endpoints, which information is available on the FortiSASE software installations page? (Choose two answers)
A. The endpoint the software is installed on1
B. The license status of the software2
C. The vendor of the software3
D. The usage frequency of the software
Explanation:
This question tests your understanding of application inventory features in FortiSASE, specifically what information is displayed on the Software Installations page when monitoring potentially unwanted applications across managed endpoints. The Software Installations tab shows a global list of applications installed on all FortiSASE managed endpoints Fortinet, helping administrators track software deployments and identify security risks like PUAs.
✅ Correct Answer: A - The endpoint the software is installed on
When viewing the Software Installations tab, you can select an application and view which specific endpoints have that application installed. This endpoint visibility is critical for PUA monitoring because it allows administrators to quickly identify which devices are running potentially risky software. You can drill down from the global software list to see individual machines, making it possible to take targeted remediation actions on affected endpoints rather than organization-wide measures.
✅ Correct Answer: C - The vendor of the software
Each application list includes details such as vendor and version information. Vendor information is essential for PUA detection because it helps distinguish legitimate software from suspicious applications. Many PUAs masquerade as legitimate tools but come from unknown or untrustworthy vendors. Having vendor details displayed allows administrators to quickly assess software legitimacy and make informed decisions about whether to block or allow specific applications based on their source.
❌ Incorrect Answer: B - The license status of the software
Software license status is not displayed on the FortiSASE Software Installations page. The platform focuses on security-relevant metadata like which endpoints have software installed and who published it, rather than licensing compliance information. License management falls outside the scope of FortiSASE's primary function as a SASE security platform. Organizations needing license tracking would use dedicated software asset management tools rather than relying on FortiSASE's PUA monitoring capabilities.
❌ Incorrect Answer: D - The usage frequency of the software
Usage frequency metrics are not provided on the Software Installations page. FortiSASE tracks what software exists on endpoints and basic identifying information, but doesn't monitor application execution patterns or how often users launch specific programs. While usage analytics would be valuable for risk assessment, the platform prioritizes inventory visibility and threat detection over behavioral analytics. The focus remains on identifying what's installed rather than measuring how actively it's being used.
What is the purpose of the grace period for off-net endpoints in the FortiSASE Network Lockdown feature? (Choose one answer)
A. To allow users to attempt VPN reconnection before restrictions are applied1
B. To bypass security policies for specific applications
C. To permanently block network access for non-compliant endpoints
D. To automatically reset the FortiClient configuration
Explanation:
The grace period in FortiSASE Network Lockdown provides a brief window during which off-net endpoints can attempt to re-establish a secure connection—typically via VPN—before full network restrictions are enforced. This prevents abrupt service disruption and allows compliant devices time to reconnect securely.
✅ Correct Answer:
A. To allow users to attempt VPN reconnection before restrictions are applied
When an endpoint is detected as off-net (i.e., not connected through the approved secure tunnel), FortiSASE initiates a grace period. During this interval, the endpoint retains limited network access to facilitate reconnection to the corporate network via FortiClient VPN. This ensures legitimate users aren’t immediately locked out due to transient connectivity issues, supporting a seamless and secure user experience.
❌ Incorrect Answers:
B. To bypass security policies for specific applications
This is incorrect because the grace period does not exempt any application from security policies. All traffic remains subject to enforcement; the grace period only delays full lockdown to allow reconnection, not policy bypass.
C. To permanently block network access for non-compliant endpoints
This misrepresents the feature’s intent. The grace period is temporary and designed to avoid immediate blocking. Permanent blocking may occur only after the grace period expires and the endpoint remains non-compliant.
D. To automatically reset the FortiClient configuration
FortiSASE does not use the grace period to modify or reset FortiClient settings. Configuration management is handled separately through endpoint compliance policies, not the Network Lockdown grace mechanism.
Reference:
Fortinet official documentation - FortiSASE
| Page 1 out of 12 Pages |
| 123456 |
Choosing the right preparation material is critical for passing the Fortinet NSE 7 FortiSASE 25 Enterprise Administrator exam. Here’s how our NSE7_SSE_AD-25 practice test is designed to bridge the gap between knowledge and a passing score.